The SAMLSSO plugin requires an enterprise license.
#
This plugin is for advanced users in an organization using SAML. While this config is generic in its description for all SAML providers, see the Microsoft ADFS config example for specifics on it. *SAMLSSO_ADFS*
This plugin can be linked together with the WebApplication plugin for a scenario where your LDAP does not apply to your SAML logins. *SAMLSSO_WebApplication*
1)
#
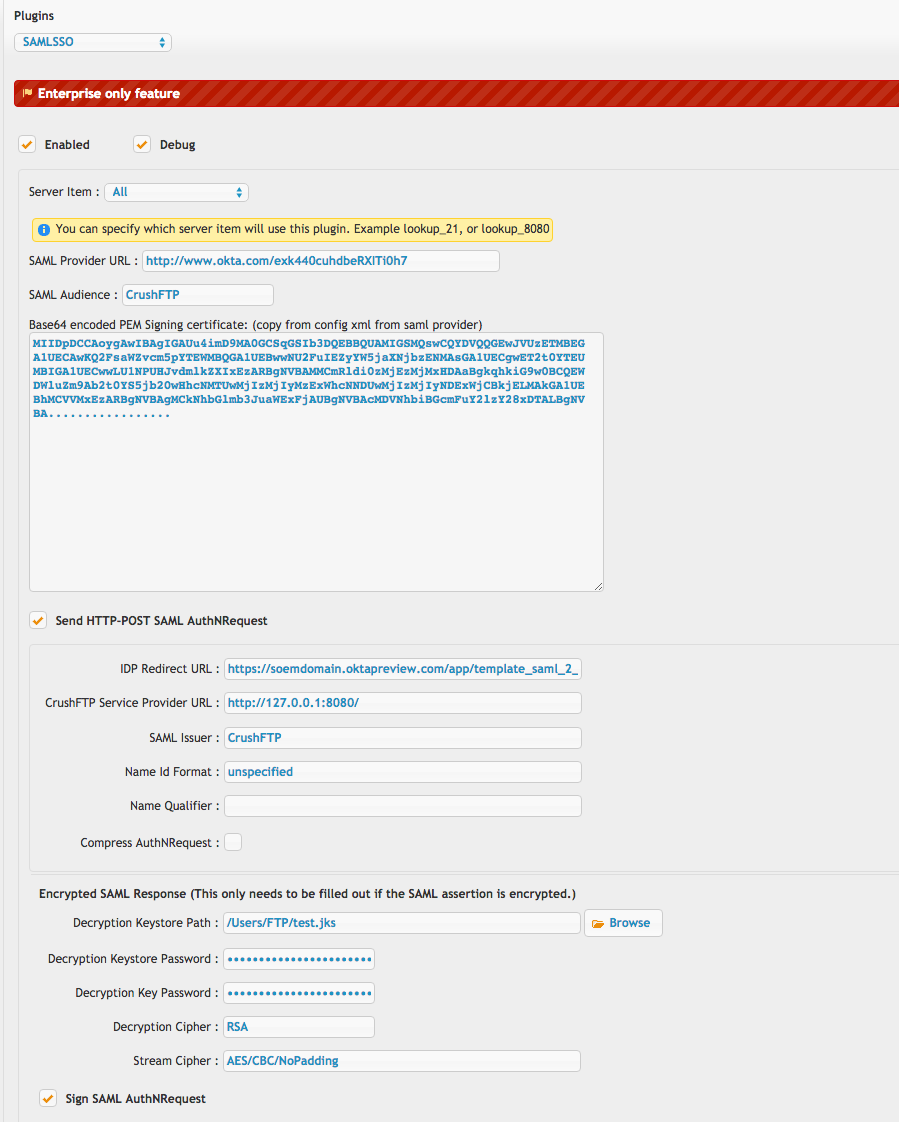
The top half controls the connection parameters to the SAML provider server.We provide an example screenshot for an OKTA account. Both HTTP POST and redirect modes are supported.
2)
#
The lower half controls what to do with the resulting user that is validated once they are redirected back to your CrushFTP server. This mainly contains configuration items related to LDAP. An LDAP server is required for looking of role associations for the user that SAML validated.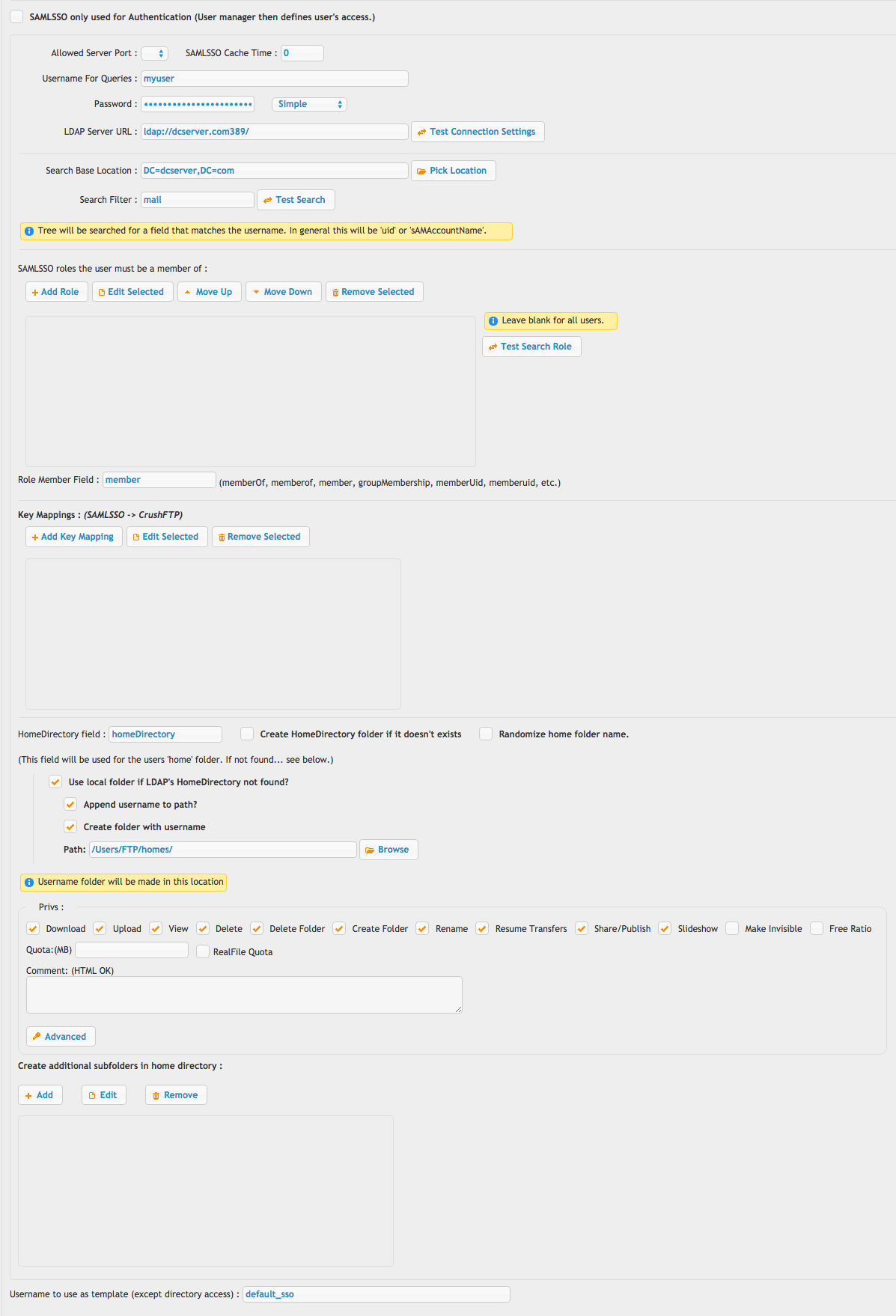
3)
#
The final item is using a Url like this to make CrushFTP redirect a user to the SAML provider.http://domain.com/?u=SSO_SAML&p=redirectThis could be placed on your login page, or even use javascript to auto redirect the user to that URL.
Be certain the Preferences, Misc tab has the remember invalid usernames configured to 0 seconds or your SAML login will get rejected since CrushFTP caches the username as being invalid and doesn't even ask the plugin.
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
«
This particular version was published on 29-Dec-2020 05:25 by Ben Spink.
G’day (anonymous guest)
Log in
JSPWiki
