CrushFTP-specific terms used in this wiki, and related:
- Groups
- a logical way to organize user accounts, our term for an Organizational Unit equivalent, there is a separate wiki on this
- Inheritance
- a way to automatically apply user settings from one user to another. The term roots in object oriented programming, there is a separate wiki on this
- Group Template account
- inheritance parent or archtype account, that parents inheritance for a group of user accounts
- VFS Linking
- loosely related to inheritance, a pointer to a VFS directory of another user account, there is a separate wiki on this
You can delegate administration allowing a limited administrator to create and manage users in their group, and assign folders that they themselves have access to. Both the administrator account and the related group member accounts will be confined to a specific top level VFS directory, with the admin having full access on the directory and grant subfolders underneath to group member accounts. Nor the admin or the users can escalate their directory access level beyond that, we call this the Group Root
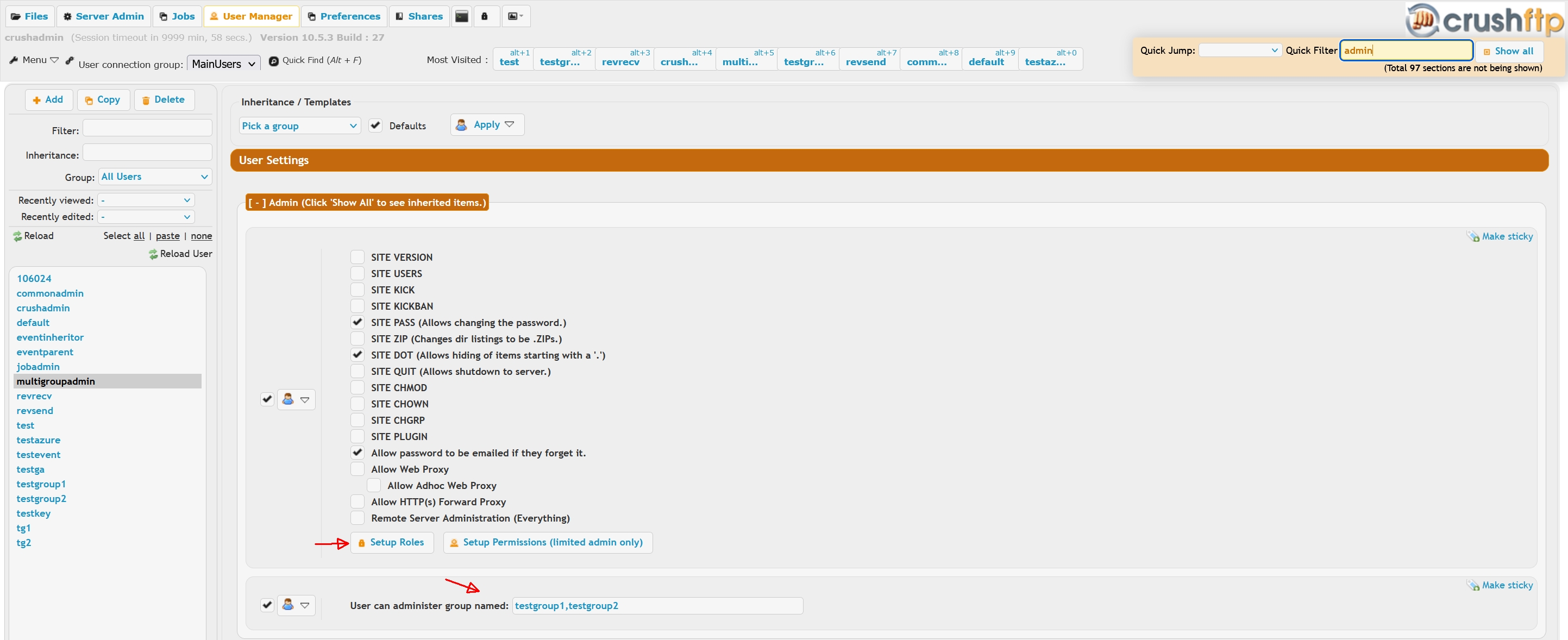 |
There are two different checkboxes. One for "Everything" and one for "Limited". If you enable the "Limited" checkbox, the user who logs in to do remote admin will only get the user manager interface.
The user manager will only contain a list of users who are part of a group that you granted this administrator access to.
So if test3 is a limited admin, there must be a group named "sub_admin" in my example. The sub_admin group should not have test3 as a member, or else test3 can edit themselves.
There must also be a user named "sub_admin" which has a VFS with the folders you want the admin to be able to work with.
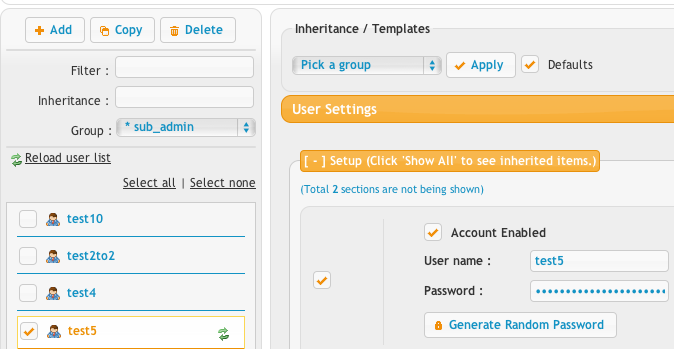
Security is enforced when the admin goes to save a change to a user. The server verifies any change the remote admin submits.
1.) If the user is not a member of the group, the change is rejected.
2.) If the home folders being specified are not a sub folder of the home directory that the group user can access, the change is rejected.
3.) If the change involves adding an event to a user that specifies a "plugin" action, the change is rejected.
4.) Other admin escalation permissions are denied too.
These are done to enforce security and prevent privilege escalation. Any attempted violation of these is logged in the server log for audit purposes.
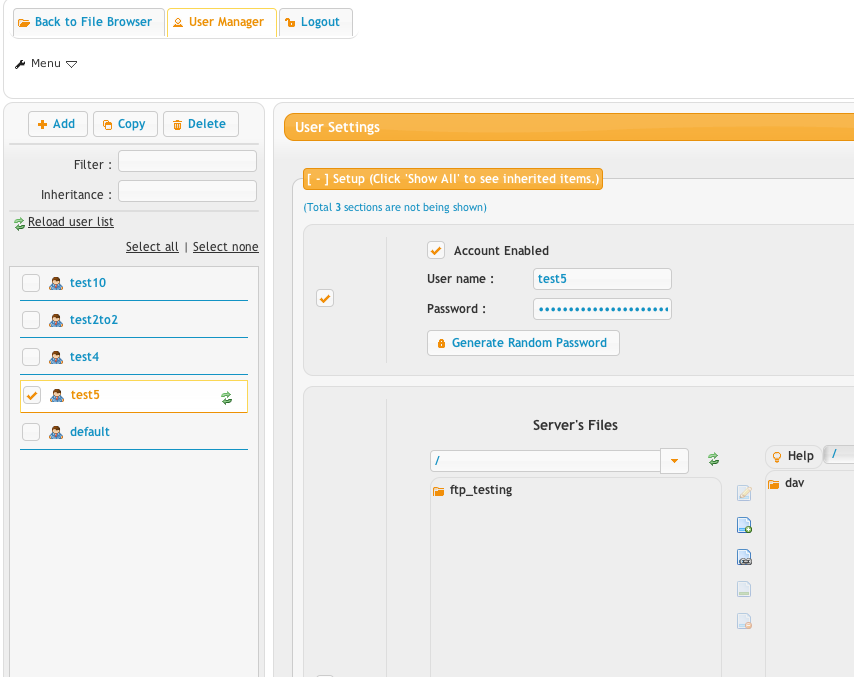
Finally the view from a limited admin when they login.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
jpg |
admin_restricted_base.jpg | 523.6 kB | 1 | 17-Oct-2023 20:03 | Ada Csaba | |
jpg |
admin_restricted_permissions.j... | 206.3 kB | 1 | 17-Oct-2023 20:03 | Ada Csaba | |
jpg |
admin_restricted_roles.jpg | 338.8 kB | 1 | 17-Oct-2023 20:03 | Ada Csaba | |
jpg |
admin_restricted_view.jpg | 176.4 kB | 1 | 17-Oct-2023 21:45 | Ada Csaba | |
png |
limited_admin.png | 50.1 kB | 3 | 29-Dec-2020 05:25 | Ben Spink | |
png |
limited_group.png | 45.5 kB | 1 | 29-Dec-2020 05:25 | Ben Spink | |
png |
limited_view.png | 55.3 kB | 1 | 29-Dec-2020 05:25 | Ben Spink |
