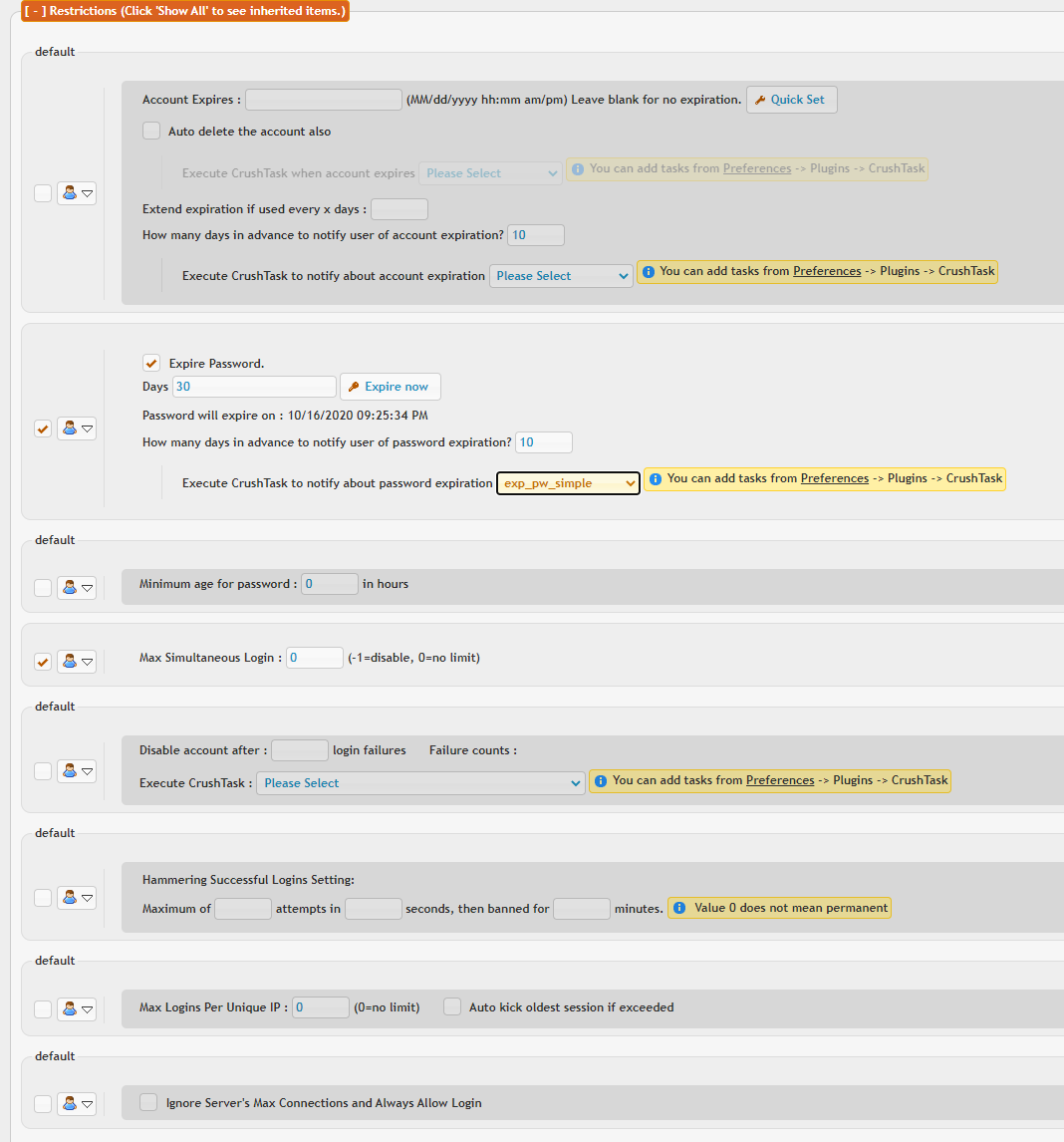
Account expires lets you set an expiration for an account on a certain date. You can also set the flag to delete the account from the user manager once its expired. The extend expiration allows you to keep the account expiration rolling further into the future as long as the user remains active enough. If they login once every 30 days, extend it for 30 more days from the current date.
Expire password will force the user to change their password every X number of days.
Max simultaneous logins controls how many times this username can be logged in at once. Be extremely careful setting this to a restrictive value as clients will have trouble connecting. For instance, web browsers often need at least 8.
Max logins per unique IP lets you control how many logins from each IP are allowed. The anonymous account may be limited to 3 connections from any given IP, but allow 50 people in total to be using the username. This makes sure one person isn't using all 50 logins.
Ignore server's max connections will allow a special account (usually an admin account) to login even when the server is rejecting other user accounts because its 'full'. This option does not override your license maximum.
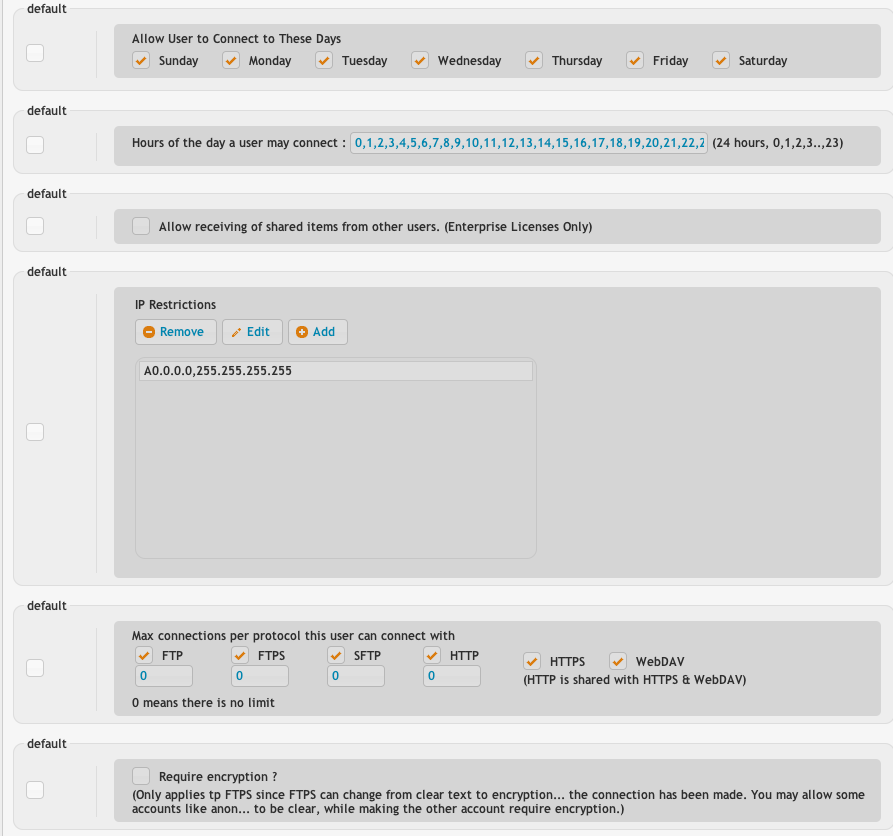
Days of the week lets you control what days a user can login on.
Hours of the day lets you control what hours of the day are allowed.
Allow receiving shared items from other users is an enterprise sonly feature. The WebInterface allows sharing between multiple users and this will allow a user to receive these items, or ignore them.
IP restrictions lets you allow certain ranges of IPs, or block IPs. Warning! If you do not have the 'A0.0.0.0,255.255.255.255' entry in there, no one can login at all. There must be at least one entry. The list is searched from top to bottom trying to find a match, and when it does, it stops looking for any more.
The protocols the user can use determines if they are allowed to use insecure protocols for example, or maybe you want to block them using WebDAV. You can also set the max logins per protocol.
Require encryption basically forces them to use FTPS on your FTP server. You may allow some users to be insecure, while enforcing it on others.
SSH public key authentication can be configured here too.
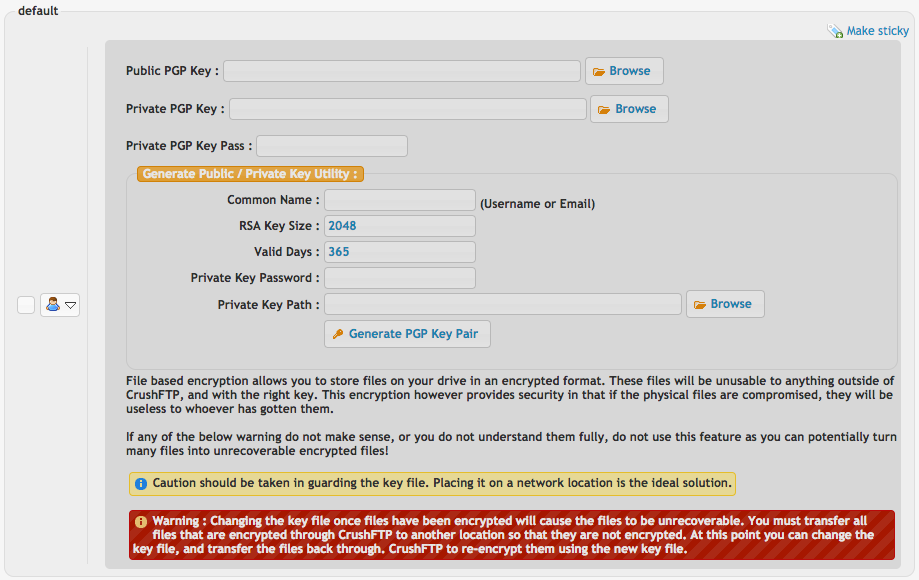
File based encryption can be enabled so that all files uploaded into this account are written to disk with PGP encryption. Here you can generate and configure the PGP key. Use this feature with caution so you don't accidentally loose the PGP key and make the data useless... Files uploaded will also be decrypted on the fly making this seamless data at rest encryption.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
file_encryption.png | 150.7 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
restrictions1.png | 68.4 kB | 3 | 29-Dec-2020 05:25 | Sandor | |
png |
restrictions2.png | 64.5 kB | 2 | 29-Dec-2020 05:25 | Ben Spink |
