Enterprise Licenses Only
#
This plugin allows you to delegate access of OAuth providers. On the CrushFTP's login page next to the login button will appear the enabled provider's "Signed in" button".Currently Google Sign-In, Microsoft Sign-In, Azure Active Directory B2C Sign in and Amazon Cognito Sign in are supported.
1. Google Sign-In
#
See Google Sign in Configuration
2. Microsoft Sign-In
#
See Microsoft Sign in Configuration
3. Azure Active Directory B2C
#
About Azure Directory B2C : https://docs.microsoft.com/en-us/azure/active-directory-b2c/overview

CrushFTP requires : Tenant name, User flow name, Client ID of the App registration.
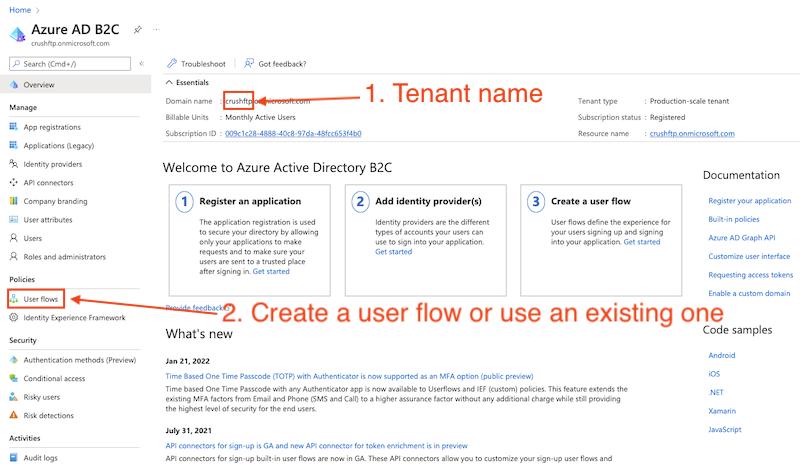
Application registration: Go to the App registrations and click on New registration:
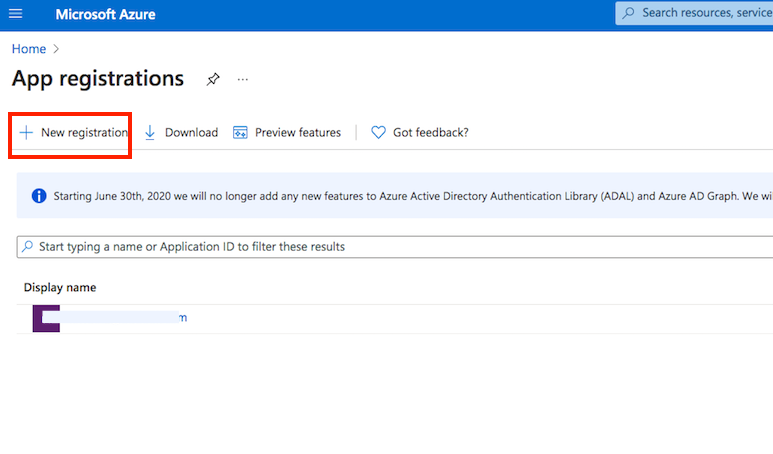
Name it. Select Single-page Application as platform. The redirect url must ends with :WebInterface/login.html. Then click on register.
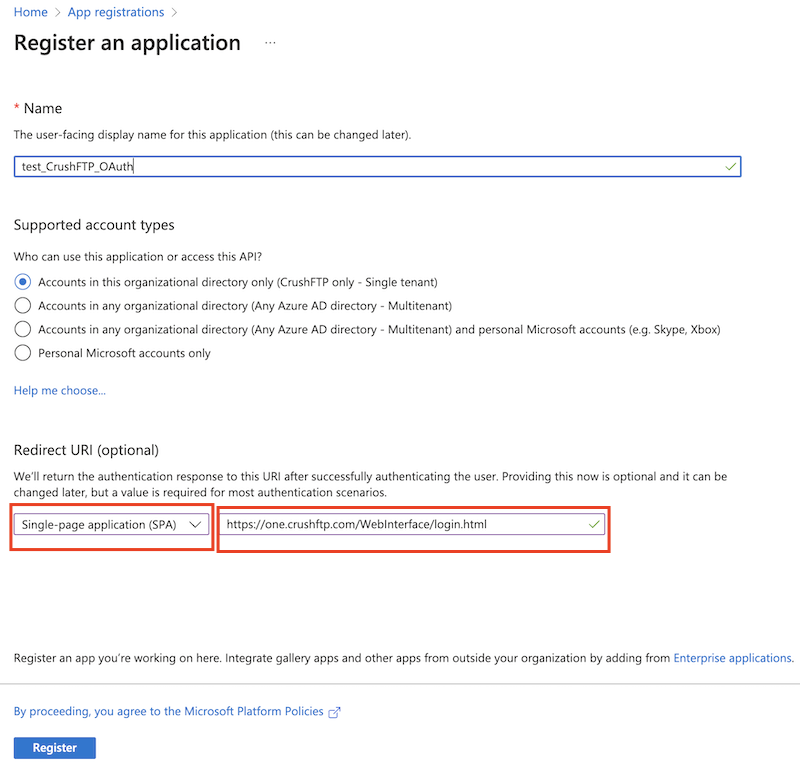
Check the flag "ID tokens (used for implicit and hybrid flows)" at Platform configurations.
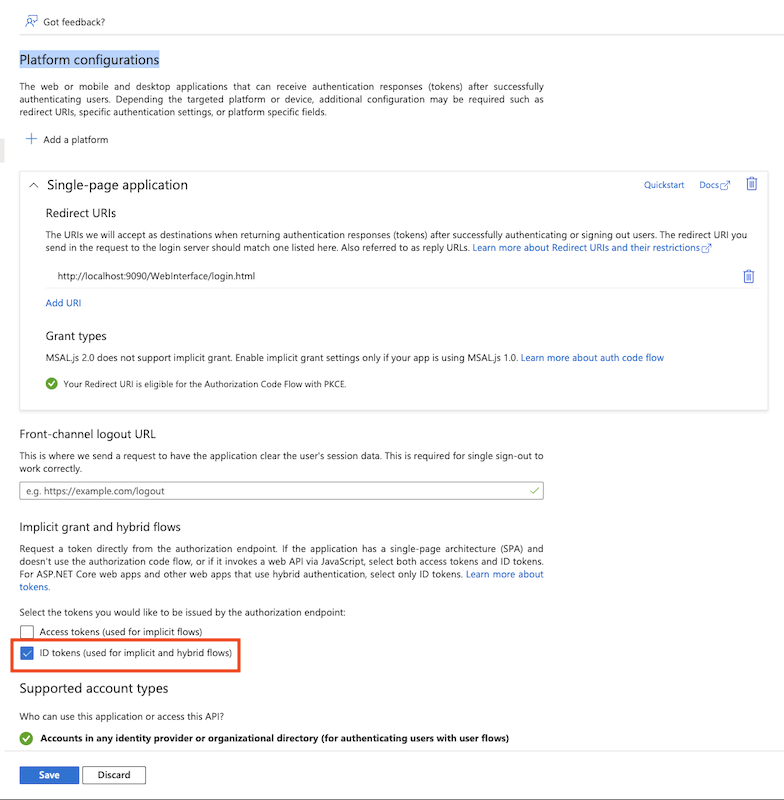
Get Application (client) ID from App registration -> Overview
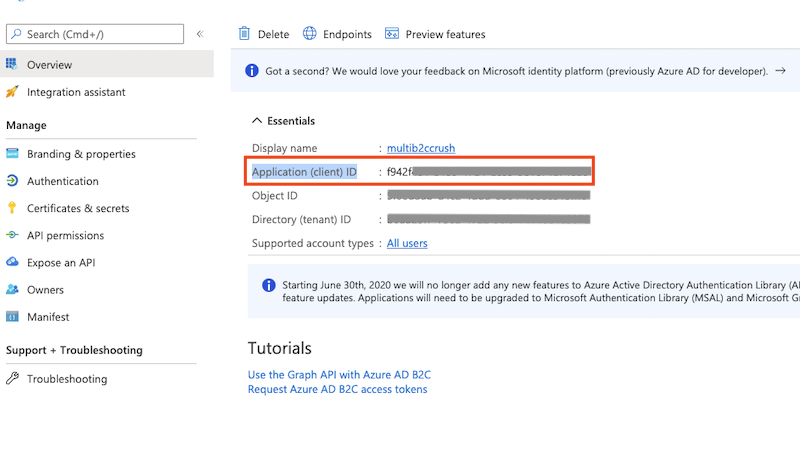
Go to the Preferences-> Ip/Servers and select the HTTP or HTTPS port item(OAuth Sign in Tab) where you want to enable the Azure Active Directory B2C button. Check the "Enable Azure Active Directory B2C Sign in" flag and provide the Tenant name, User flow name, Client ID of the App registration (mentioned above).
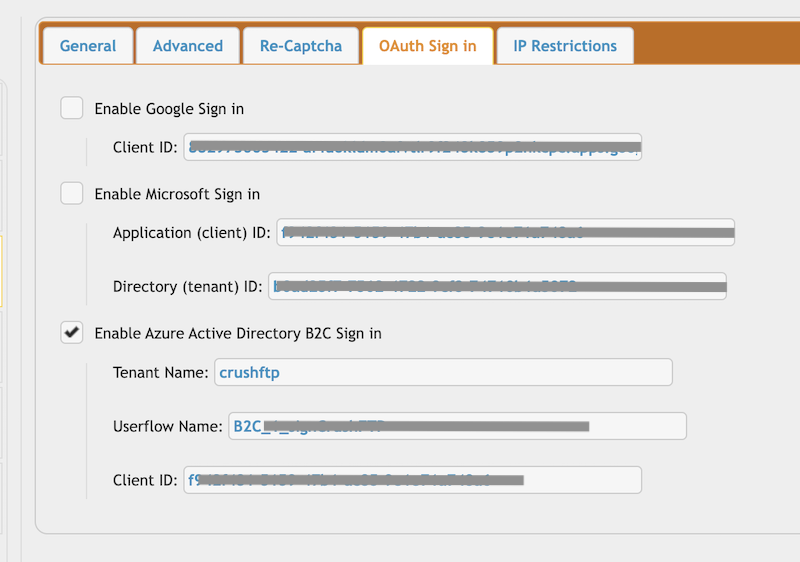
Configure the CrushOAuth plugin and enable the flag: "Enable Azure Active Directory B2C Auth".
4. Amazon Cognito
#
About Amazon Cognito : https://aws.amazon.com/cognito/
Create (https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html ) or use one of your existing Amazon Cognito user pool: https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html
) or use one of your existing Amazon Cognito user pool: https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html
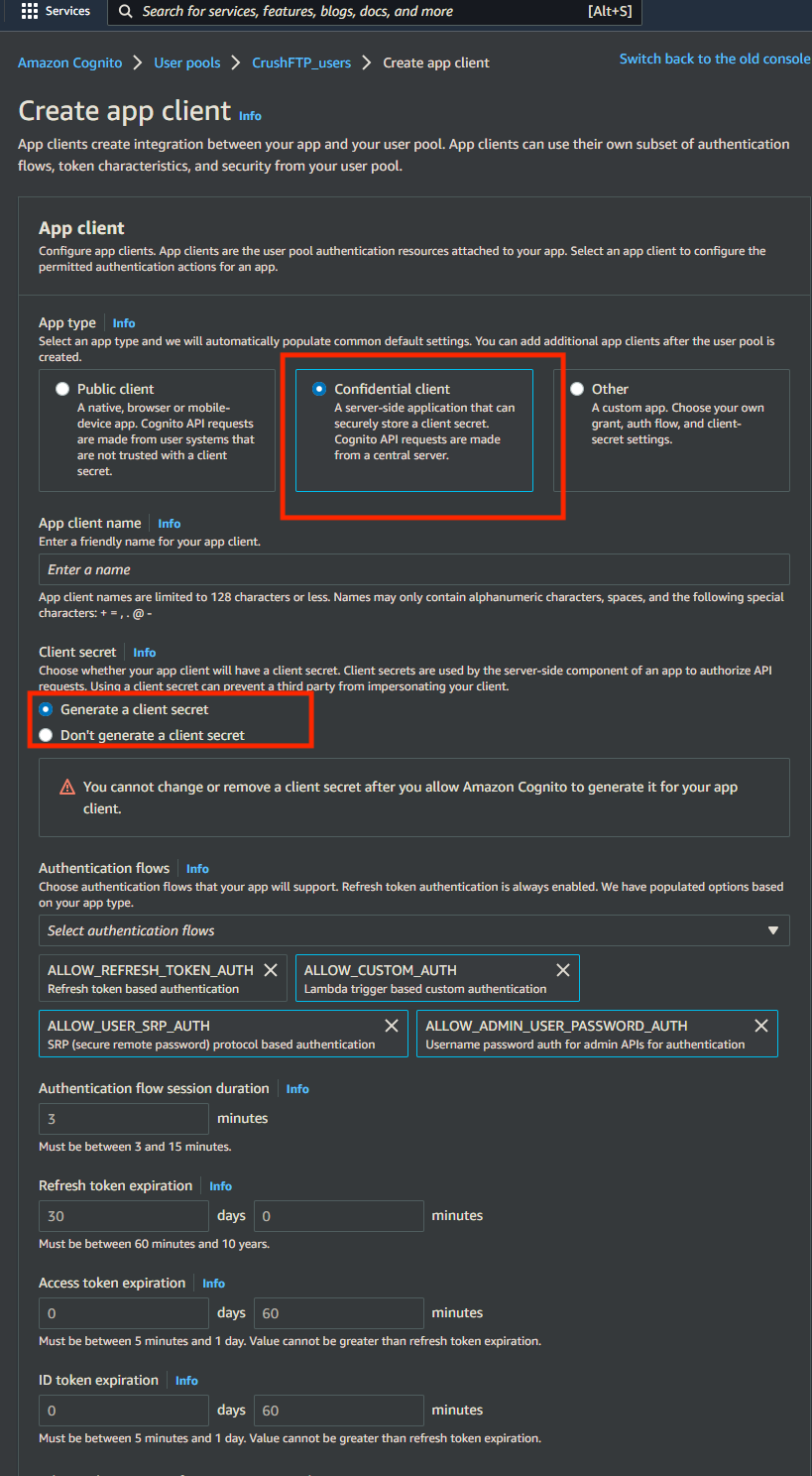
Create or configure app client of the user pool (https://docs.aws.amazon.com/cognito/latest/developerguide/user-pool-settings-client-apps.html ).
).
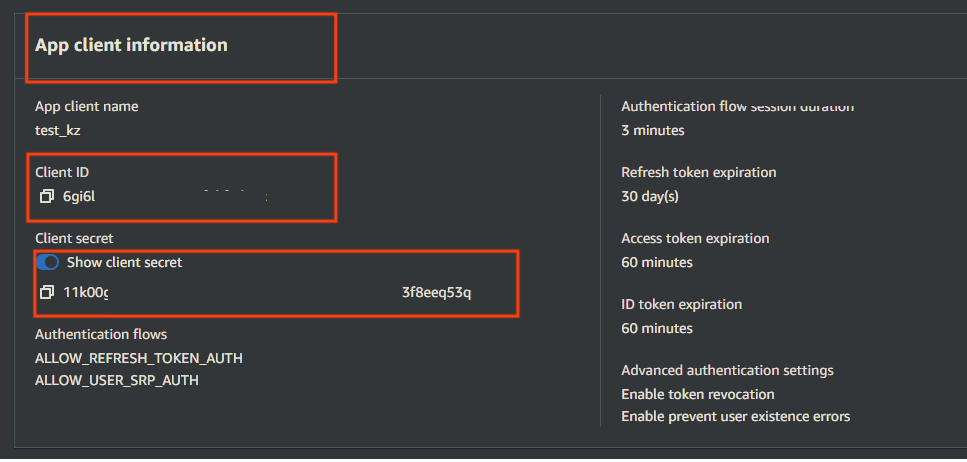
App type : Select Confidential client.
Enable Generate client secret.
Allowed callback URLs: https://your.CrushFTP.domain.com/WebInterface/login.html
OAuth 2.0 grant types : Authorization code grant
OpenID Connect scopes : OpenID
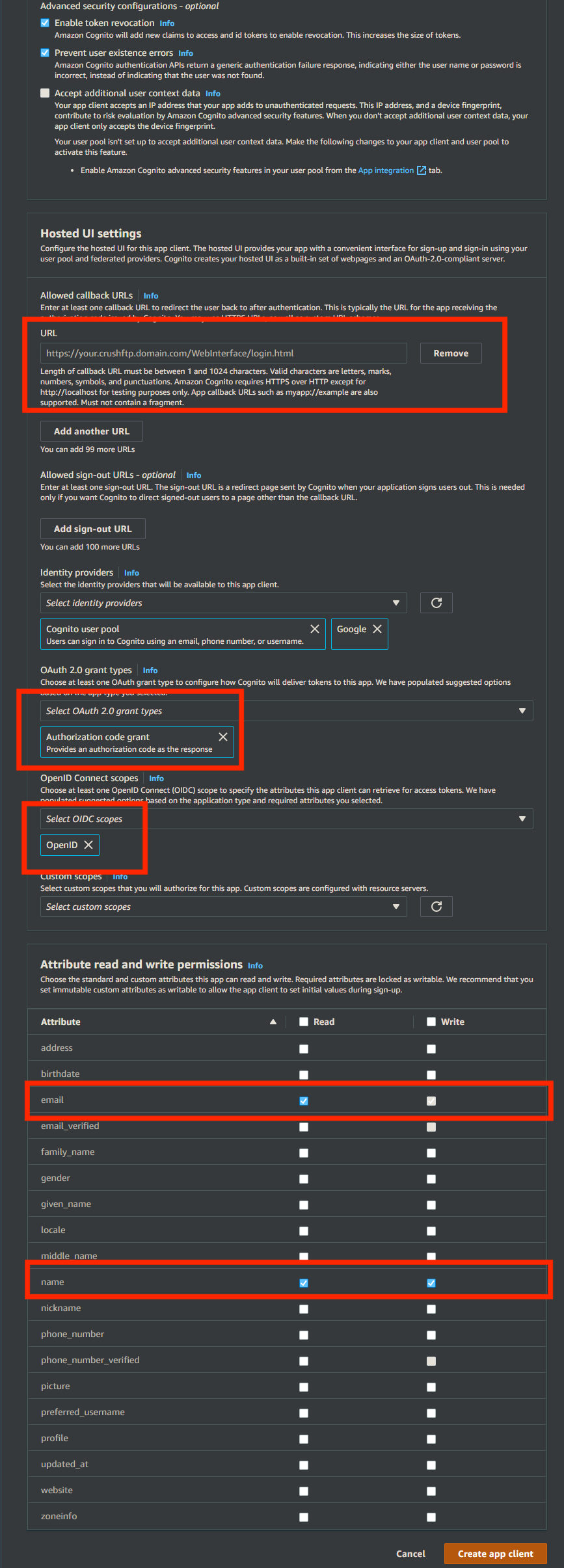
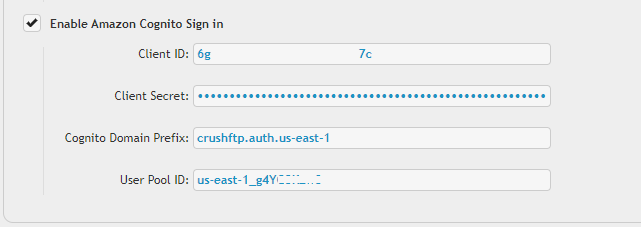
Go to the Preferences-> Ip/Servers and select the HTTP or HTTPS port item(OAuth Sign in Tab) where you want to enable the Amazon Cognito Sing-In button. Check the "Enable Amazon Cognito Sign in" flag.
Required info from App client of the User Pool : Client ID and Client Secret.
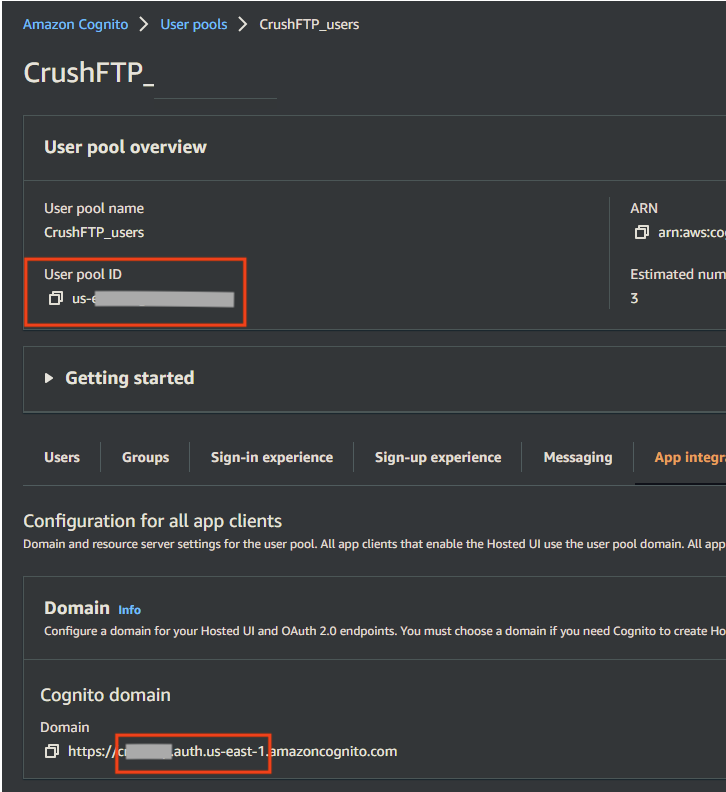
Required info from User Pool :
Cognito Domain Prefix: It is part of the Cognito domain (Amazon console -> Amazon Cognito -> User Pools -> User poll -> App integration tab). It also contains the region of the User Pool.
Like:
[domain_name].auth.[amazon region]
User pool ID
Configure the CrushOAuth plugin and enable the flag: Enable Amazon Cognito Auth.
5. Plugin Settings
#
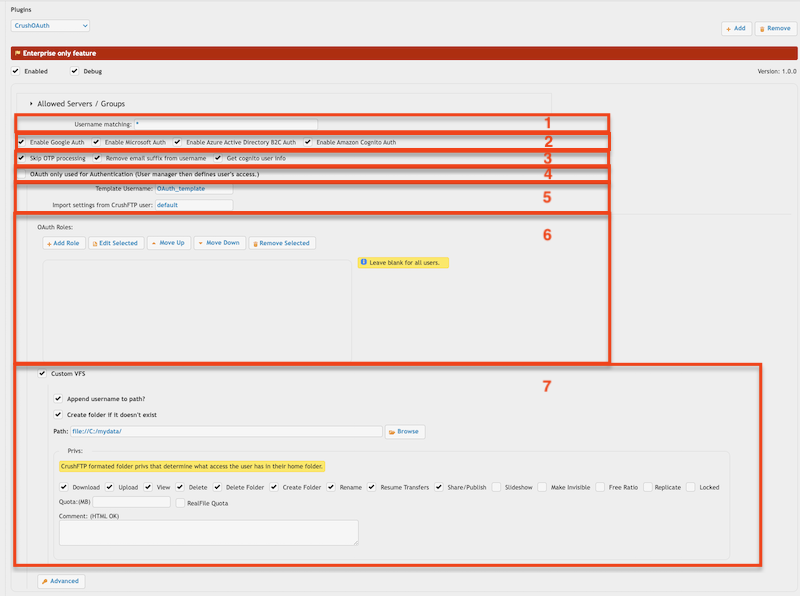
1. Username matching -> It filters the OAuth user name (Google Auth: email address, Microsoft Auth: user principle name). You can put multiple value separated by comma. Domain filter is allowed to (like *mydomain.com).
2. Allowed authentication types
3. OAuth only used for Authentication (User manager then defines user's access.) -> If the users already exists with username of the OAuth, you can use the plugin just for authentication.
4. Template Username -> The signed in user inherits no just the settings, but the VFS items too (as Linked VFS).
Import settings from CrushFTP user -> The signed in user inherits just the settings from this user. It must have a value! Default value would be : default -> the default user of CrushFTP
5. VFS related settings : You can also assign a VFS item for the signed in user.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
app_reg_auth_config.png | 160.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_reg_config.png | 173.1 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_azure_settings.png | 184.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_client_id.png | 127.2 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_id_token.png | 207.0 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_client_id_secret.png | 66.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool.png | 82.3 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_1... | 244.9 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_2... | 340.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
dmz_template_user_internal_por... | 94.7 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
g_sign_origin_redirect_url.png | 85.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
gsign_in_button.png | 204.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
http_port_oauth_item_settings.... | 43.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
plugin_settings.png | 99.6 kB | 7 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings.png | 76.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_b2c.png | 105.6 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_cognito.png | 14.1 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_ms.png | 75.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz |