Constraint: Enterprise Licenses Only
This plugin allows you to delegate access to OAuth (https://en.wikipedia.org/wiki/OAuth ) providers. On the CrushFTP's login page next to the login button will appear the enabled provider's "Signed in" button".
) providers. On the CrushFTP's login page next to the login button will appear the enabled provider's "Signed in" button".
Currently Google Sign-In, Microsoft Sign-In, Azure Active Directory B2C Sign in and Amazon Cognito Sign in are supported.
1. Google Sign-In
#
See Google Sign in Configuration2. Microsoft Sign-In
#
See Microsoft Sign in Configuration3. Azure Active Directory B2C
#
See Azure Active Directory B2C Configuration4. Amazon Cognito
#
See Amazon Cognito ConfigurationDMZ
#
Configure your OAuth settings on the DMZ's HTTP or HTTPS port item.
Plugin Settings
#
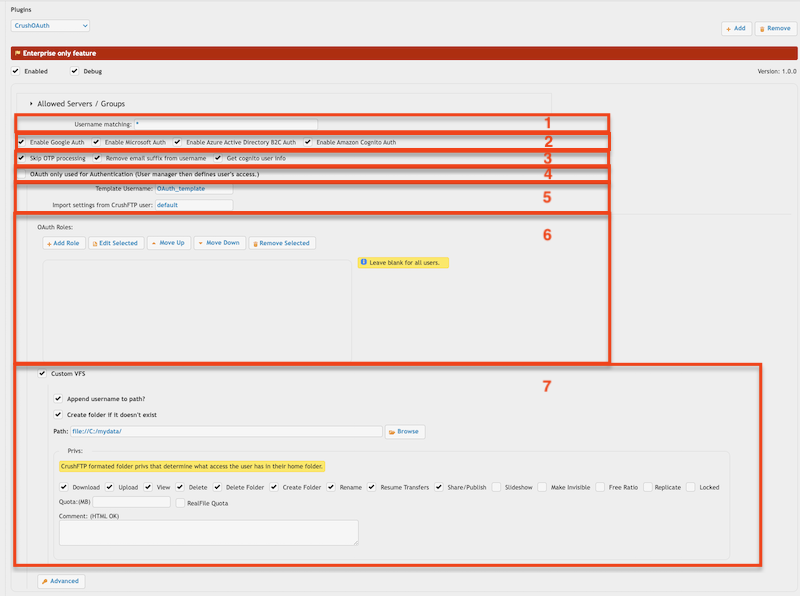
1. Username matching -> It filters the OAuth user name (Google Auth: email address, Microsoft Auth: user principal name). Allow multiple values separated by a comma. Domain filter is allowed (like *mydomain.com).
2. Allowed authentication types: Google Sign-In, Microsoft Sign-In, Azure Active Directory B2C Sign in and Amazon Cognito Sign. Configure the sign-in button on HTTP(S) server.
3.
a. Skip OTP processing: CrushOAuth plugin is not compatible with OTP Settings as IDP (identity provider) can have its own two-factor authentication. Turning the flag to true will skip OAuth users from CrushFTP's OTP process.
b. Remove email suffix from username: It removes the email suffix of the user name. Like username "my_user@email.com" will be "my_user".
c. Get Cognito user info: Gets more info about Amazon Cognito users (like custom attributes). It is related only to Amazon Cognito Sign in.
4. OAuth only used for Authentication (User Manager defines user's access.) -> If users already exist in CrushFTP's User Manager, you can use the CrushOAuth plugin just for authentication.
5. Template Username -> The signed-in user inherits not just the settings, but the VFS items too (as Linked VFS).
Import settings from CrushFTP user -> The signed-in user inherits just the settings from this user. It must have a value! Default value would be : default -> the default user of CrushFTP
6 OAuth Roles -> You can configure different Template Users (see 5.) based on IDP's (identity provider) attributes.
IDP Attribute examples:
Google Sign-In: email_verified, idp_user_info, given_name, family_name, email_verified, group Microsoft Sign-In: mail, idp_user_info, displayName, jobTitle, businessPhones, mobilePhone, officeLocation, group Amazon Cognito Sign-in: email, username, identities, cognito:username, cognito:groups, custom:<<defined custom attributes>>Role examples :
<<IDP attribute name>>=<<IDP attribute value>>,<<IDP attribute name>>=<<IDP attribute value>> : tmeplate user name Like: cognito:groups=Azure_SAML,custom:groups:test_group_one or cognito:groups=*SAML*,custom:groups:test_group_one or cognito:groups=REGEX:.*SAML$,custom:groups:test_group_one
IDP attribute value: Exact match, Simple Match (like *mail.com*), Regex match (like REGEX:<<the regular expression>>), if the value is an array you can reference only one of the array element (exact match only). Like (IDP Attribute value -> groups:["group1","group2"] -> you can match with group1)
7. VFS-related settings -> You can set custom VFS for CrushOAuth users.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
app_reg_auth_config.png | 160.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_reg_config.png | 173.1 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_azure_settings.png | 184.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_client_id.png | 127.2 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_id_token.png | 207.0 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_client_id_secret.png | 66.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool.png | 82.3 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_1... | 244.9 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_2... | 340.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
dmz_template_user_internal_por... | 94.7 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
g_sign_origin_redirect_url.png | 85.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
gsign_in_button.png | 204.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
http_port_oauth_item_settings.... | 43.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
plugin_settings.png | 99.6 kB | 7 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings.png | 76.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_b2c.png | 105.6 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_cognito.png | 14.1 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_ms.png | 75.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz |