Enterprise Licenses Only
#
This plugin allows you to delegate access of OAuth providers.Currently only Google Sign in is supported.
1. Google Sign-In
#
You will start at the API credentials manager:
https://console.developers.google.com/projectselector/apis/credentials

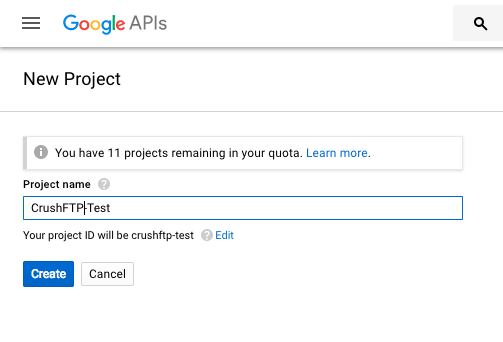
You first need to make a project. My example calls this CrushFTP-Test.
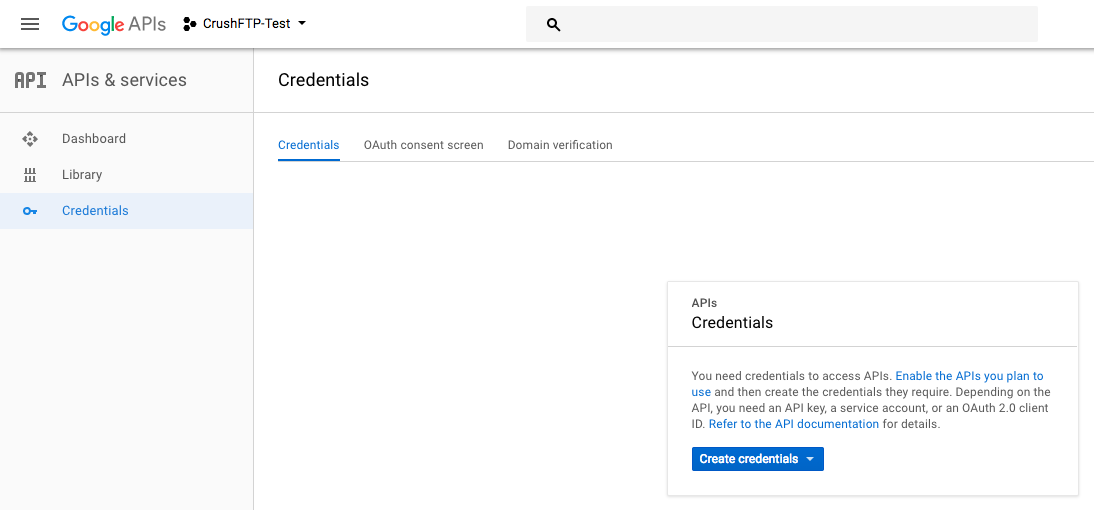
Next select create credentials, and choose the Web Application type.
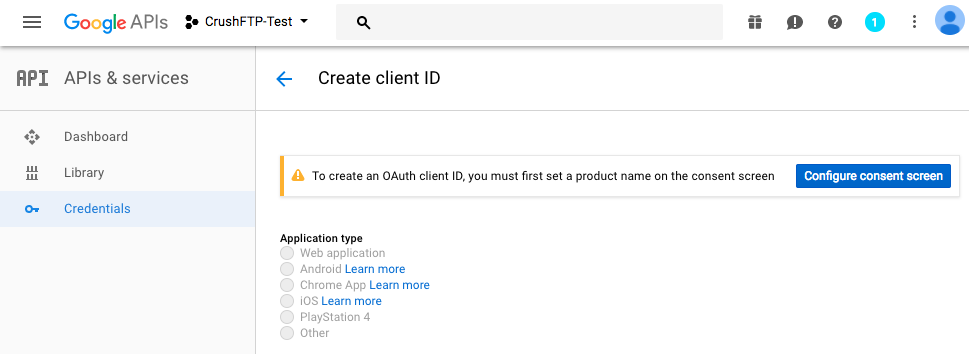
When configuring the credential, you have to tell Google the domain you will be originating from when creating the auth token, so this is the URL you use for server administration. Just the protocol://dns_or_ip:port Don't have a trailing slash or it will complain.
You also need to put in the redirect URL of where Google is going to send back the Id token (Id Token : That will be used for authentication of the google user). Copy the Client ID that will be required to integrate the Google Sing-In Button.
Integrate Google Sign-In button
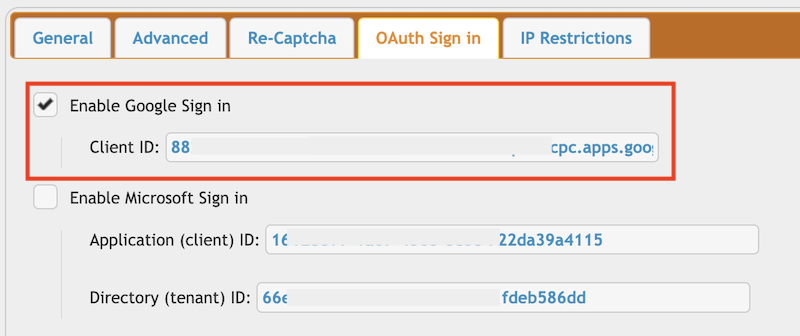
Go to the Preferences-> Ip/Servers and select the HTTP or HTTPS port item where you want to enable the Google Sing-In button. Check the "OAuth Sign in" flag and provide the Client ID of you Google project(mentioned above).
2. Microsoft Sign-In
#
It requires Microsoft Graph Application registration. Start at the Microsoft azure portal:
https://azure.microsoft.com/en-us/features/azure-portal/

Application registration: Go to the App registrations and click on New registration:
attachments
Plugin Settings
#
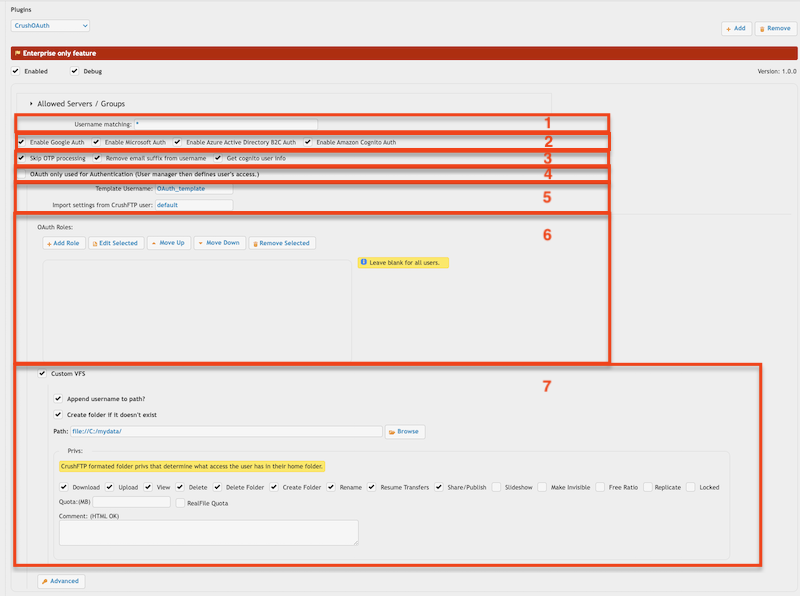
1. Username matching -> It filters the OAuth user name (Google Auth: email address, Microsoft Auth: user principle name). You can put multiple value separated by comma. Domain filter is allowed to (like *mydomain.com).
2. Allowed authentication types
3. OAuth only used for Authentication (User manager then defines user's access.) -> If the users already exists with username of the OAuth, you can use the plugin just for authentication.
4. Template Username -> The signed in user inherits no just the settings, but the VFS items too (as Linked VFS).
Import settings from CrushFTP user -> The signed in user inherits just the settings from this user.
5. VFS related settings : You can also assign a VFS item for the signed in user.
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
app_reg_auth_config.png | 160.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_reg_config.png | 173.1 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_azure_settings.png | 184.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_client_id.png | 127.2 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
b2c_id_token.png | 207.0 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_client_id_secret.png | 66.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool.png | 82.3 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_1... | 244.9 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
cognito_user_pool_app_client_2... | 340.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
dmz_template_user_internal_por... | 94.7 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
g_sign_origin_redirect_url.png | 85.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
gsign_in_button.png | 204.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
http_port_oauth_item_settings.... | 43.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
plugin_settings.png | 99.6 kB | 7 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings.png | 76.4 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_b2c.png | 105.6 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_cognito.png | 14.1 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
port_item_settings_ms.png | 75.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz |
«
This particular version was published on 05-Dec-2023 05:32 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki