The plugin supports OpenID Connect (https://en.wikipedia.org/wiki/OpenID
 ), an authentication protocol built on top of the OAuth 2.0 (https://en.wikipedia.org/wiki/OAuth
), an authentication protocol built on top of the OAuth 2.0 (https://en.wikipedia.org/wiki/OAuth ) authorization framework.
) authorization framework.!!! Constraints: It only works through HTTP or HTTPS protocol. Authorization Code Flow is supported (Implicit Flow or Hybrid Flow are not supported). It requires Enterprise License.
1. Identity Provider's (IdP) general configuration
#
The plugin requires the following IdP information and configuration:• Client ID
• Client Secret: Authorization Code Flow requires it.
• Redirect URL: The redirect URL is the endpoint in your IdP application where the IdP directs the user after successful authentication. This URL receives the authorization code or access token as part of the authentication process. The redirect URL must target the CrushFTP server and conclude with /SSO_OIDC/. Like:
https://yourCrushFTP.domain.com/SSO_OIDC/
Google: https://support.google.com/googleapi/answer/6158849

2. Plugin Configuration
#
2.1 IdP related settings
#
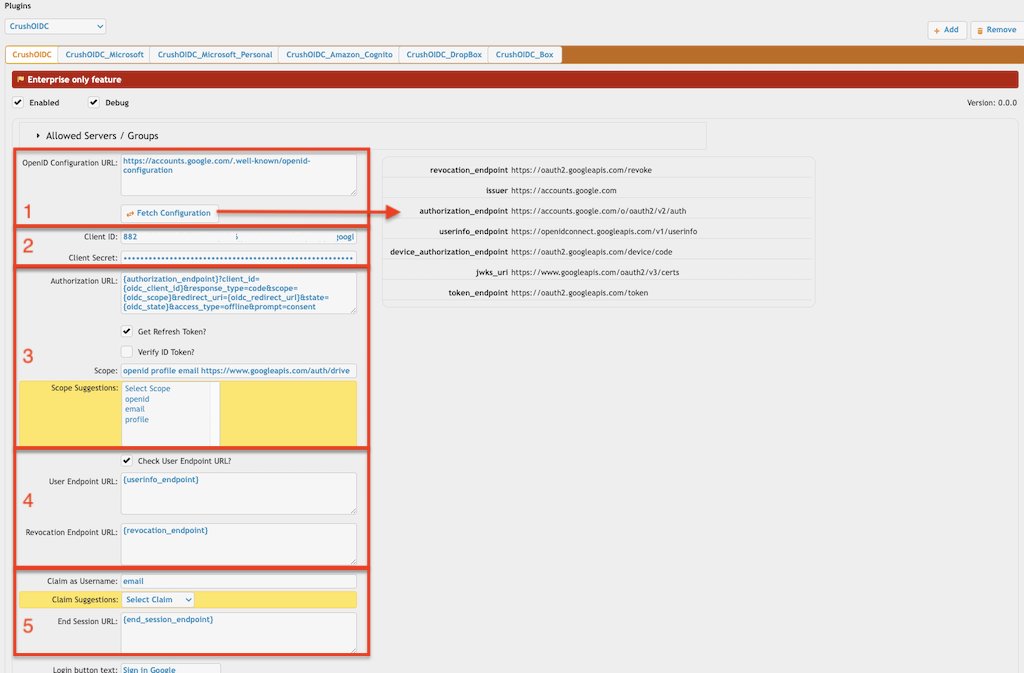
2.1.1 OpenID Configuration URL:
Dynamic endpoint:
This HTTP URL is part of the OpenID Connect (OIDC) Discovery mechanism. It follows a standard called RFC 5785 (https://datatracker.ietf.org/doc/html/rfc5785
 ), which defines the use of .well-known URIs for discovering metadata about services. It queries this HTTP endpoint to configure itself dynamically, avoiding hard-coded values. The retrieved JSON document includes important endpoints and details like:
), which defines the use of .well-known URIs for discovering metadata about services. It queries this HTTP endpoint to configure itself dynamically, avoiding hard-coded values. The retrieved JSON document includes important endpoints and details like:• Authorization endpoint
• Token endpoint
• User info endpoint
• Supported scopes and claims
• Public keys for verifying tokens
List of .well-known URLs for various identity providers and services that support OpenID Connect (OIDC):
Google: https://accounts.google.com/.well-known/openid-configuration
Microsoft Azure AD: https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration
Microsoft Azure B2C: https://{tenant_name}.b2clogin.com/{tenant_name}.onmicrosoft.com/{policy}/v2.0/.well-known/openid-configuration
Amazon (Cognito): https://cognito-idp.{region}.amazonaws.com/{userPoolId}/.well-known/openid-configuration
Okta: https://{yourOktaDomain}/.well-known/openid-configuration
Auth0: https://{yourDomain}.auth0.com/.well-known/openid-configuration
Dropbox: https://www.dropbox.com/.well-known/openid-configuration
Local endpoint:
You can reference a local JSON file if the identity provider (IdP) does not support OpenID Connect but does support OAuth 2.0 (like Box cloud storage). Instead of specifying an HTTP URL, provide the path to a local JSON file, such as:
./box_open_id_config.json
The JSON file should include the authorization endpoint. Example for Box cloud storage:
{
"authorization_endpoint":"https://account.box.com/api/oauth2/authorize",
"token_endpoint":"https://api.box.com/oauth2/token"
}
2.1.2 App registration related informations:
Client ID: Provide the Client ID (the unique identifier) of your IdP.
Client Secret: Provide the Client Secret of your IdP.
2.1.3 Authorization related settings:
Authorization URL: It is the endpoint where IdP initiates the authentication and authorization process. The default configuration would be:
{authorization_endpoint}?client_id={oidc_client_id}&response_type=code&scope={oidc_scope}&redirect_uri={oidc_redirect_url}&state={oidc_state}
Variables:
• {authorization_endpoint}: Authorization URL of IdP. Retrieved from the OpenID Configuration JSON.
• {oidc_client_id}: Client Id of the IdP.
• {oidc_scope}: Reference the provided "Scope"(s) of plugin.
• {oidc_redirect_url}: Autogenerated value. The URL redirects the user after successful authentication. It must match the redirect URL registered and configured in the IdP.
• {oidc_state}:
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
oidc_crushftp_related_settings... | 97.6 kB | 2 | 23-Sep-2025 03:10 | krivacsz | |
png |
oidc_dmz_plugin_settings.png | 141.0 kB | 2 | 09-Jan-2025 23:13 | krivacsz | |
png |
oidc_dropbox_settings.png | 58.1 kB | 1 | 19-May-2025 05:22 | krivacsz | |
png |
oidc_gdrive_settings.png | 71.2 kB | 1 | 19-May-2025 05:25 | krivacsz | |
png |
oidc_general_plugin_settings.p... | 39.3 kB | 1 | 09-Jan-2025 07:32 | krivacsz | |
png |
oidc_gstorage_settings.png | 67.4 kB | 1 | 19-May-2025 05:51 | krivacsz | |
png |
oidc_idp_related_plugin_settin... | 176.0 kB | 3 | 09-Jan-2025 23:17 | krivacsz | |
png |
oidc_key_mappings.png | 23.4 kB | 1 | 23-Sep-2025 03:20 | krivacsz | |
png |
oidc_login_buttons.png | 59.4 kB | 1 | 09-Jan-2025 07:50 | krivacsz | |
png |
oidc_onedrive_settings.png | 71.6 kB | 1 | 19-May-2025 04:24 | krivacsz | |
png |
oidc_redirect_base_setting.png | 37.0 kB | 1 | 05-Feb-2025 03:55 | krivacsz | |
png |
oidc_sharepoint2_settings.png | 74.6 kB | 1 | 19-May-2025 05:18 | krivacsz |
«
This particular version was published on 09-Jan-2025 03:09 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki