The plugin supports OpenID Connect SSO ( more info: https://en.wikipedia.org/wiki/OpenID
 ), an authentication protocol built on top of the OAuth 2.0 (https://en.wikipedia.org/wiki/OAuth
), an authentication protocol built on top of the OAuth 2.0 (https://en.wikipedia.org/wiki/OAuth ) authorization framework.
) authorization framework.!!! Constraints: It only works through HTTP or HTTPS protocol. Authorization Code Flow is supported (Implicit Flow or Hybrid Flow are not supported). It requires Enterprise License.
1. Identity Provider's (IdP) general configuration
#
The plugin requires the following IdP information and configuration:• Client ID
• Client Secret: Authorization Code Flow requires it.
• Redirect URL: The redirect URL is the endpoint in your IdP application where the IdP directs the user after successful authentication. This URL receives the authorization code or access token as part of the authentication process. The redirect URL must target the CrushFTP server and conclude with /SSO_OIDC/. Like:
https://your.domain.com/SSO_OIDC/
Google: https://support.google.com/googleapi/answer/6158849

2. Plugin Configuration
#
2.1 IdP related settings
#
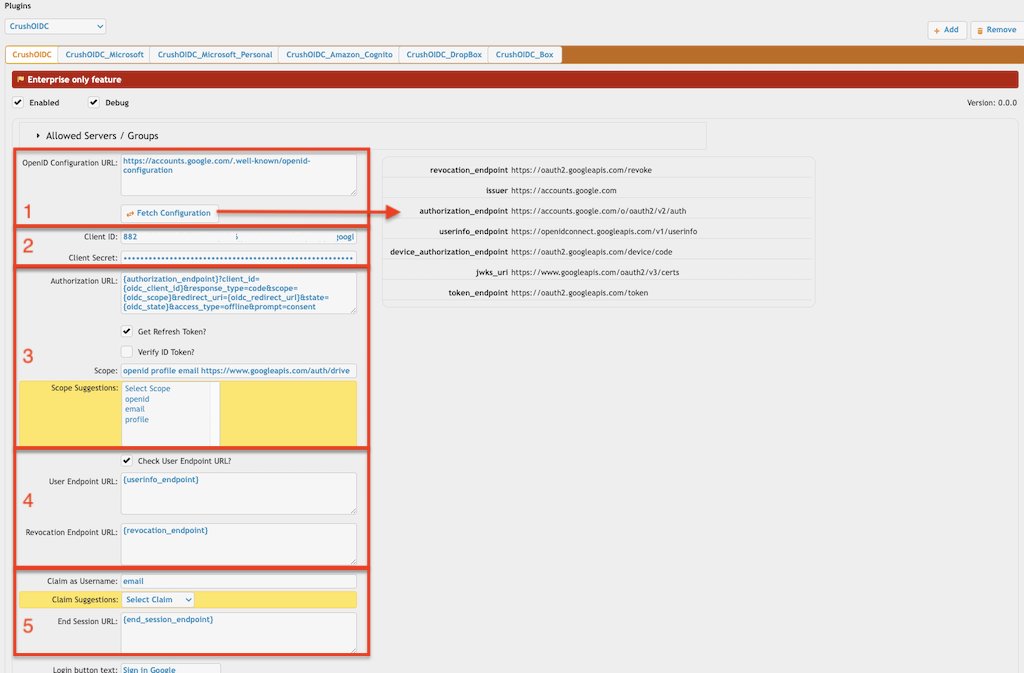
2.1.1 OpenID Configuration URL (Required):
#
Dynamic endpoint:
This HTTP URL is part of the OpenID Connect (OIDC) Discovery mechanism. It follows a standard called RFC 5785 (https://datatracker.ietf.org/doc/html/rfc5785
 ), which defines the use of .well-known URIs for discovering metadata about services. It queries this HTTP endpoint to configure itself dynamically, avoiding hard-coded values. The retrieved JSON document includes important endpoints and details like:
), which defines the use of .well-known URIs for discovering metadata about services. It queries this HTTP endpoint to configure itself dynamically, avoiding hard-coded values. The retrieved JSON document includes important endpoints and details like:• Authorization endpoint
• Token endpoint
• User info endpoint
• Supported scopes and claims
• Public keys for verifying tokens
List of .well-known URLs for various identity providers and services that support OpenID Connect (OIDC):
Google: https://accounts.google.com/.well-known/openid-configuration
Microsoft Azure AD: https://login.microsoftonline.com/{tenant_id}/v2.0/.well-known/openid-configuration
Microsoft Azure B2C: https://{tenant_name}.b2clogin.com/{tenant_name}.onmicrosoft.com/{policy}/v2.0/.well-known/openid-configuration
Amazon (Cognito): https://cognito-idp.{region}.amazonaws.com/{userPoolId}/.well-known/openid-configuration
Okta: https://{yourOktaDomain}/.well-known/openid-configuration
Auth0: https://{yourDomain}.auth0.com/.well-known/openid-configuration
Dropbox: https://www.dropbox.com/.well-known/openid-configuration
Local endpoint:
You can reference a local JSON file if the identity provider (IdP) does not support OpenID Connect but does support OAuth 2.0 (like Box cloud storage). Instead of specifying an HTTP URL, provide the path to a local JSON file, such as:
./box_open_id_config.json
The JSON file should include the authorization endpoint. Example for Box cloud storage:
{
"authorization_endpoint":"https://account.box.com/api/oauth2/authorize",
"token_endpoint":"https://api.box.com/oauth2/token"
}
2.1.2 App registration related informations:
#
Client ID: Provide the Client ID (the unique identifier) of your IdP.
Client Secret: Provide the Client Secret of your IdP.
2.1.3 Authorization related settings (Required):
#
Authorization URL: It is the endpoint where IdP initiates the authentication and authorization process. The default configuration would be:
{authorization_endpoint}?client_id={oidc_client_id}&response_type=code&scope={oidc_scope}&redirect_uri={oidc_redirect_url}&state={oidc_state}
Variables:
• {authorization_endpoint}: Authorization URL of IdP, retrieved from the OpenID Configuration JSON.
• {oidc_client_id}: Client ID assigned by the IdP during app registration. Retrieved from plugin's "Client ID" setting.
• {oidc_scope}: Specifies the "Scope"(s) provided by the plugin to determine the level of access.
• {oidc_redirect_url}: An autogenerated URL by CrushFTP, composed of the initial host and port, followed by /SSO_IDC/. This URL is used to redirect the user after successful authentication. !!! It must exactly match the redirect URL registered and configured in the IdP.
• {oidc_state}: An autogenerated value by CrushFTP to maintain the state between the authentication request and callback. This is used to prevent CSRF attacks.
Scope: It defines the permissions or access levels requested by CrushFTP during the authentication process. The scopes determine the type of information (claims) IdP will include in the ID token and what resources the client application can access. (like user profile information, email address, and cloud storage access). Commonly supported scope values include:
openid profile email
Scope Suggestions: Displays possible scope values based on the OpenID configuration data.
Get Refresh Token: It is used to access the user's cloud storage through the IdP. It adjusts the Authorization URL by appending the following parameters:
access_type=offline&prompt=consent
• The access_type=offline parameter is used in the Authorization URL in OpenID Connect (OIDC) and OAuth 2.0 flows to request a refresh token from the IdP. A refresh token allows the application to obtain new access tokens without requiring the user to log in again, enabling offline access.
The refresh token enables access to the user's cloud storage through the IdP. CrushFTP supports cloud storage integration with services such as Google Drive (GDriveSetup), OneDrive (OneDriveSetup), SharePoint (SharePoint Integration), and Dropbox (Dropbox Integration).
When integrating cloud storage, ensure the "Scope" parameter includes the necessary permissions for accessing the user's cloud storage. Add the following scopes for the respective services:
Google: https://www.googleapis.com/auth/drive Dropbox: files.metadata.write files.content.write files.content.read
Microsoft does not require additional scopes for this purpose. Ensure that the App Registration includes the "Files.ReadWrite.All" permission, configured as either Delegated or Application. More info at SharePoint Integration.
At "Custom VFS" settings you can reference the gained refresh token as variable:
{oidc_refresh_token}
• The prompt=consent parameter is used in the authorization URL to explicitly request the user's consent during the authentication process. This parameter ensures that the Identity Provider (IdP) displays a consent screen, even if the user has previously authorized the application.
Verify ID Token: The Authorization Code Flow uses the code value returned by the IdP to obtain the ID token. Although this step is not mandatory in the OpenID protocol, you can enable an additional verification of the returned ID token by selecting this checkbox. !!! This feature works only if the OpenID configuration includes the "jwks_uri" endpoint. It provides an extra layer of validation for the ID token.
2.1.4 IdP User endpoint:
#
Check User Endpoint URL?: This option enables CrushFTP to retrieve additional information about the user from the IdP via the "user_info" endpoint URL. !!! This feature only works if the OpenID configuration includes a "userinfo_endpoint" URL or if you manually specify it in the "User Endpoint URL" input field.
The "userinfo_endpoint" is a key component of the OpenID Connect (OIDC) protocol, providing a standardized way to retrieve additional user information from the IdP after authentication. It complements the information included in the ID token by allowing the client application to fetch more detailed and up-to-date user attributes.
Revocation Endpoint URL: The revocation endpoint is an optional endpoint in OIDC and OAuth 2.0 that allows client applications to revoke access tokens and refresh tokens issued by the IdP. Revoking a token ensures that it can no longer be used to access protected resources or obtain new tokens.
Refresh Token: The refresh token will be revoked at the end of the CrushFTP session.
Access Token:
- If no refresh token is retrieved, the access token will be revoked during the plugin authentication process.
- If a refresh token is present, only the refresh token will be revoked, as revoking the access token inherently invalidates any associated refresh tokens sent by the IdP.
2.1.6 Claim and IdP session related configs:
#
Claim as Username (Required): Specify the name of the claim within the IdP's response that should be used as the username for the CrushFTP session.
!!! If this claim is not present or its value is missing in the IdP's response (either within the ID Token or retrieved from the user endpoint), the authentication will fail due to a missing username.
Claim Suggestions: Displays possible claim values based on the OpenID configuration data.
End Session URL: This URL is called at the end of the CrushFTP session to terminate the user's session. You can use the "end_session_endpoint" provided in the OpenID configuration data by referencing it as the variable {end_session_endpoint}, or you can specify the URL manually.
2.2 CrushFTP related plugin settings:
#
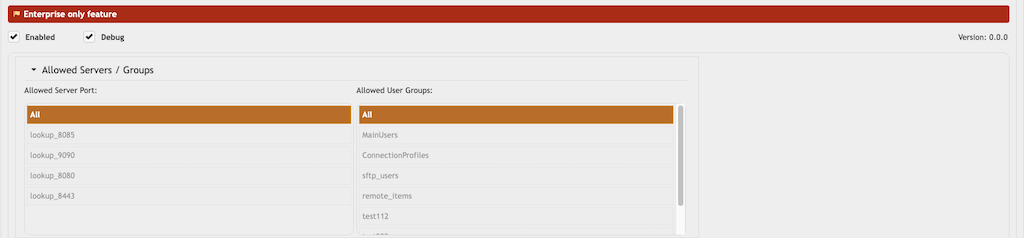
Enable: Activate the plugin. (Required)
Debug: Enable detailed logging of plugin activities. This helps troubleshoot issues. Set the debug level to 1 and at "Log File Options" check the flag "GENERAL" (see Logging).
Allowed Servers/Groups: Each plugin instance can restrict the allowed users to certain Server Ports or Sever Connection Groups (see IP Servers). To deselect the currently selected option, use ALT + Click (or ⌥ + Click on macOS).
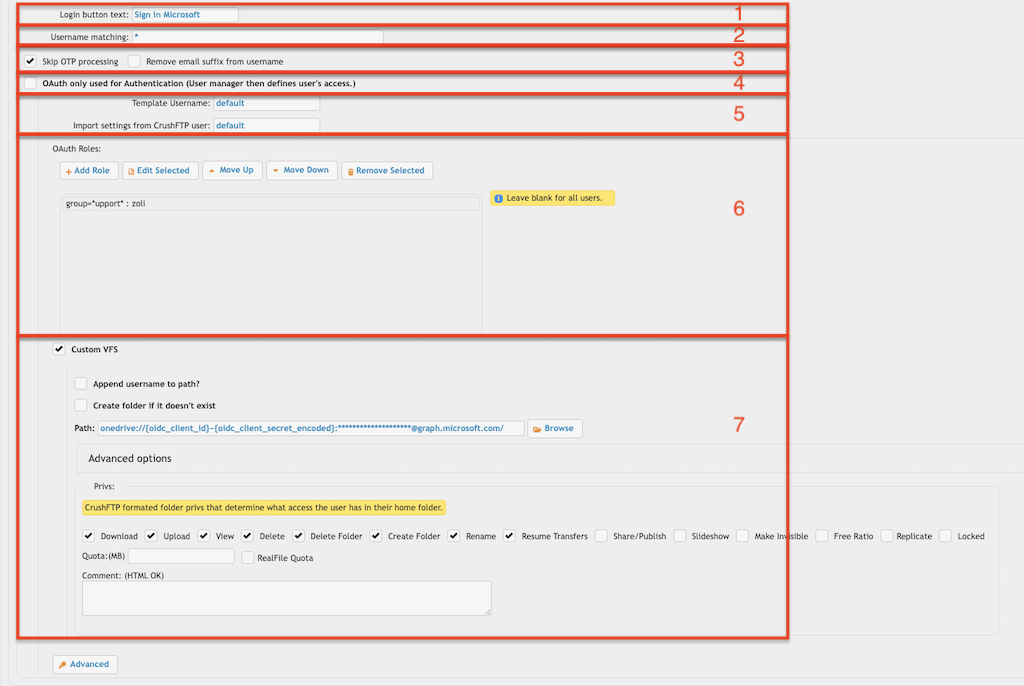
2.2.1 Login Button (Required):
#
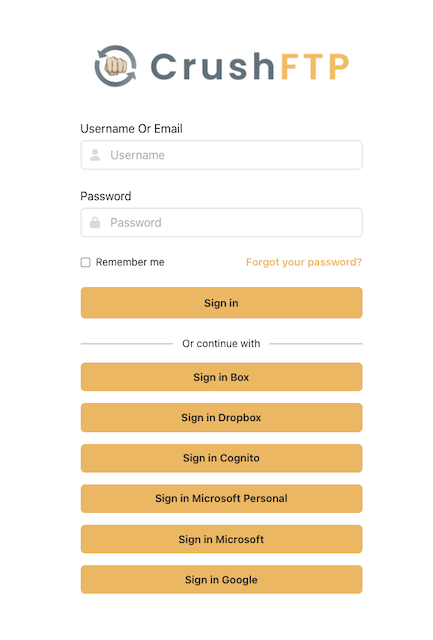
Login button text: Specify the text to display on the login button. This button will only be visible on the designated "Server Port."(allowed at "Allowed Servers/Groups") Users can authenticate through multiple Identity Providers by configuring multiple CrushOIDC plugin instances. Like:
2.2.2 Username matching (Required):
#
It filters usernames based on the value configured in "Username matching". The default value (*) allows all users. Multiple values can be specified, separated by commas. Domain filtering is also supported (Like: *mydomain.com).
IdPs that do not support tenant-based app registrations generally use a global, centralized app registration model. In such cases, applications are registered once and are not tied to a specific tenant or organizational boundary. To manage access effectively, domain filtering is often necessary (Like: Google, Dropbox).
2.2.3.1 Skip OTP processing:
#
CrushOIDC plugin is not compatible with OTP Settings, as the IdP may implement its own two-factor authentication. Enabling this flag will exclude plugin users from CrushFTP's OTP process.
2.2.3.2 Remove email suffix from username:
#
It removes the email suffix from the username. For example, the username "my_user@email.com" will be transformed to "my_user".
2.2.4 OpenID/OAuth only used for Authentication:
#
(User Manager defines user's access.) -> If users already exist in CrushFTP's User Manager, you can use the CrushOIDC plugin just for authentication.
2.2.5 User Templates (Required):
#
Template Username: The signed-in user inherits both the settings and the VFS items(as Linked VFS). It must have a value!
Import settings from CrushFTP user: The signed-in user inherits only the settings from the specified user. It must have a value!
Default value: default -> the default user of CrushFTP
2.2.6 Roles:
#
You can configure different Template Users (see 5.) based on IdP claims.
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
oidc_crushftp_related_settings... | 97.6 kB | 2 | 23-Sep-2025 03:10 | krivacsz | |
png |
oidc_dmz_plugin_settings.png | 141.0 kB | 2 | 09-Jan-2025 23:13 | krivacsz | |
png |
oidc_dropbox_settings.png | 58.1 kB | 1 | 19-May-2025 05:22 | krivacsz | |
png |
oidc_gdrive_settings.png | 71.2 kB | 1 | 19-May-2025 05:25 | krivacsz | |
png |
oidc_general_plugin_settings.p... | 39.3 kB | 1 | 09-Jan-2025 07:32 | krivacsz | |
png |
oidc_gstorage_settings.png | 67.4 kB | 1 | 19-May-2025 05:51 | krivacsz | |
png |
oidc_idp_related_plugin_settin... | 176.0 kB | 3 | 09-Jan-2025 23:17 | krivacsz | |
png |
oidc_key_mappings.png | 23.4 kB | 1 | 23-Sep-2025 03:20 | krivacsz | |
png |
oidc_login_buttons.png | 59.4 kB | 1 | 09-Jan-2025 07:50 | krivacsz | |
png |
oidc_onedrive_settings.png | 71.6 kB | 1 | 19-May-2025 04:24 | krivacsz | |
png |
oidc_redirect_base_setting.png | 37.0 kB | 1 | 05-Feb-2025 03:55 | krivacsz | |
png |
oidc_sharepoint2_settings.png | 74.6 kB | 1 | 19-May-2025 05:18 | krivacsz |
«
This particular version was published on 09-Jan-2025 08:42 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki