Certain plugins can be linked together with other plugins. Its a short list of just CrushLDAPGroup and Radius, as well as SAMLSSO and CrushLDAPGroup.
This allows you to have a SAML authentication process that got through its redirects and comes back to CrushFTP with the username provided by SAML. Instead of CrushFTP using this to lookup group associations directly...you can then pass the config over to the LDAP plugin to do its functions.
This special linking is done with the plugin's instance name. So the first instance of a plugin has a hard coded name and can't be changed. You disable that instance and make a new instance of the plugin. In its name you set it to the name of the other plugin to call plus a tilde and the instance name. So in this case its "CrushLDAPGroup~"...or "CrushLDAPGroup~SAMLAuth" where "SAMLAuth" is an instance name on the CrushLDAPGroup plugin. The first one was a blank instance name (the first plugin instance) while the second example was a named instance name of it.
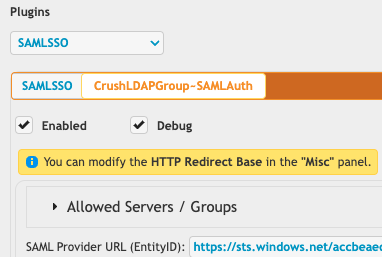
The CrushLDAPGroup plugin remains "disabled" so its not trying to process any requests. Its critical it stays disabled. It's only going to be used for validating auth when a request comes behind the scenes via inter-plugin communication from the SAML plugin.
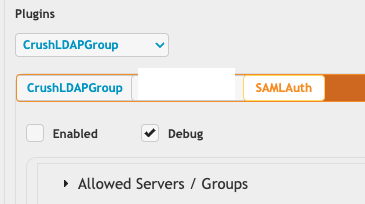
When the authentication goes through the SAML plugin, after SAML has confirmed the user, it now checks its plugin name and makes the call to the other plugin to see if it wants to add more to the plugin's auth process. if you are utilizing the SAML only does Auth, you need to turn off that checkbox temporarily, set the Cache to be -1 instead of 20, then re-enable that checkbox. otherwise you won't get the items from the LDAP plugin at all.
