Getting a valid certificate is easy with CrushFTP. (Old Portecle Guide, or Command Line Guide)
- IIS - If you already have a certificate in IIS, you can export that certificate as a .PFX file and use that certificate directly in CrushFTP. *Export IIS Certificate*
Renewing a Certificate#
Skip ahead to step 2, and create your CSR from your existing keystore files. Then continue on.New Certificate#
1.)#
Starting from scratch, go to your Preferences, Encryption, SSL tab. Click 'Generate Now' on the Step 1 section.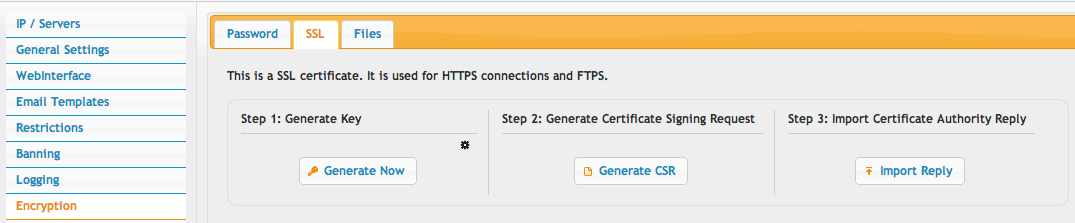
Fill in the information about your company.
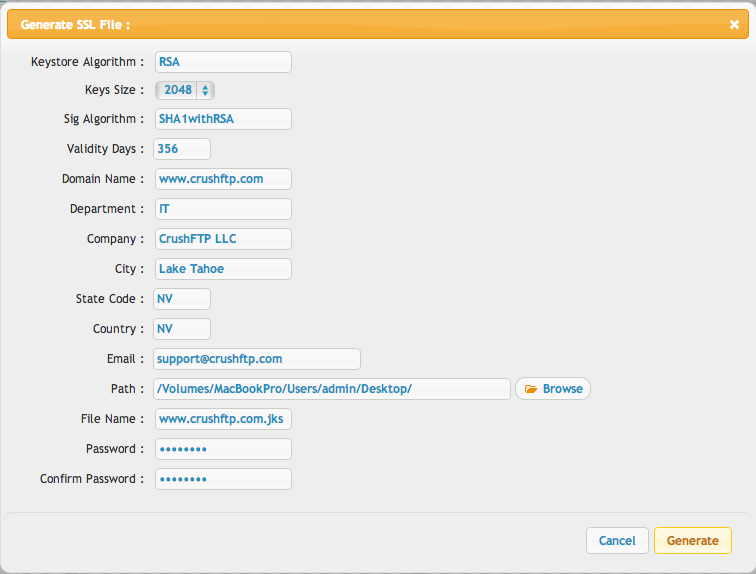
This will create the java key store for you (the .JKS file). This holds your certificate private key, the critical part you never want to loose or give away.
2.)#
Create the CSR using the Step 2 button. This CSR item is of no value except for this temporary signing step. Its your .JKS file that is *very* important, as is the password protecting it.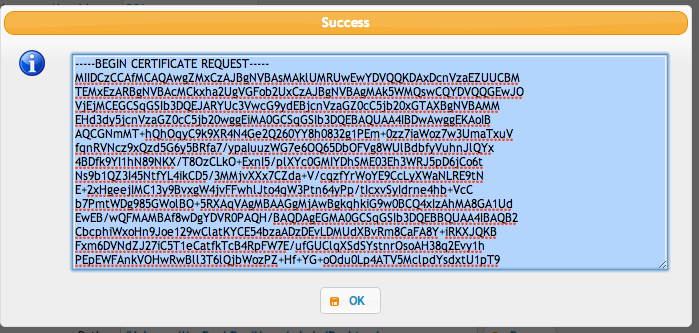
From this private key in your keystore, a Certificate Signing Request (CSR) file is generated, and this is the text that pops up for you. Copy this to your clipboard, and go paste this into your cert authority's requesting page. (GoDaddy, Verisign, DigiCert, Thawte, etc.)
3.)#
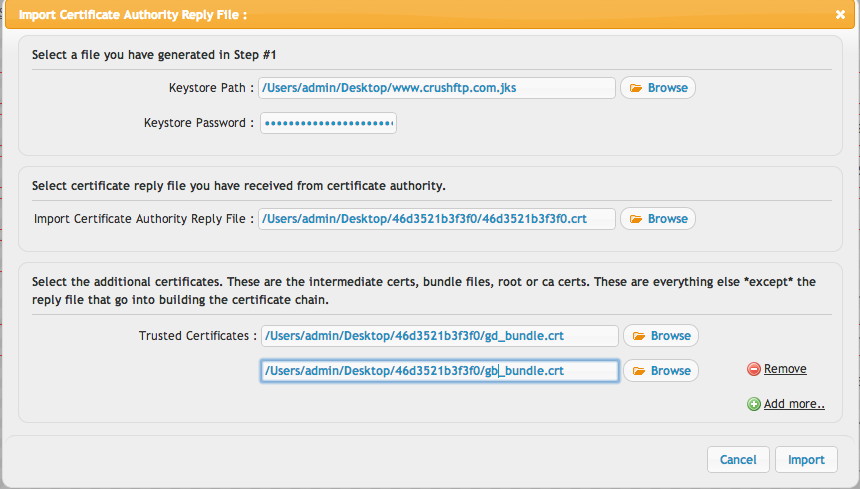
They will do their necessary verifications for the cert your requesting, and when done will give you your certificate. Now import the certificates given to you by your certificate authority. These are usually things like root, or intermediate, etc. Use the step 2 button to do this.The keystore path info is probably pre-filled out for you from the step 1. If not, fill it in, and re-enter the password.
The certificate reply file is different than the rest. Its a specific file that is only valid for your private key in your JKS keystore file. Some vendors label it with your domain name, or a series of hex characters, etc.
The trusted certs are everything else. Typically these are a bundle file, or they can be stand alone intermediate and root certificate files. Add them all here one time.
Click import, and it will report if there are any errors.
4.)#
5.)#
OBSOLETE, only for Java 8 and olderOn most Operating Systems Java ships crippled by default due to US export laws. Its extremely annoying, but you must manually copy a couple files into your java install to allow CrushFTP to use strong cryptography keys (almost all keys these days.)These policy files must be downloaded manually and installed in your Java lib/security folder.
Java6: http://www.oracle.com/technetwork/java/javase/downloads/jce-6-download-429243.html
Java7: http://www.oracle.com/technetwork/java/javase/downloads/jce-7-download-432124.html
Java8: http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
You may also search google for: 'java unlimited cryptography policy files'
OS X Java 6 install location: /System/Library/Frameworks/JavaVM.framework/Versions/CurrentJDK/Home/lib/security/
OS X Java 7 install location: /Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home/lib/security/
Windows install location: C:\Program Files\Java\jre6\lib\security\ or C:\Program Files\Java\jre7\lib\security
Don't forget to restart the Https port on Admin, ServerAdmin tab, for the changes to the certificate to take effect.
More reading to help understand the whole convoluted process of SSL.#
Every single SSL app uses the same sort of structure for SSL. So every SSL server's certs are interchangeable, they just sometimes package them in different ways that have other benefits.
The process: Before anything, a private key is created that has the "CN" attribute referencing your domain name. CN=common name. There is a bunch of other "fluff" that describes you as the company too, but the single critical element is the CN. From a private key, you can generate the (C)ertificate (S)ighning (R)equest. This describes your private key in such a way that a certificate authority (CA) can vouch that you are who you say you are, and they sign the CSR and sent you the cert (CRT) file (also known as the CA reply file). This CRT is worthless without the private key. It literally points back at that specific key's unique signature, and is 100% worthless without that private key. So that is the entire process.
Now all cert authorities also do a little more in-between...they don't sign your cert with their own super super super secret CA key, they instead sign with an intermediate certificate. The structure is something like this:
CA key (super super super secret) CA root (signed by their super super super secret) CA intermediate (signed by their root) your key (signed by their intermediate)
Everyone in the world trusts the CA key for say 10 years...and they also trust keys that it has signed. Its the "chain" of trust.
Now servers like Apache, and IIS may ask you for your private key, and the signed key. (The CSR is only useful to get the CRT, then its garbage. Don't save it thinking you have something useful...) They likely have a list of most server's intermediate and root certs, and they build a chain internally for you and use your keys.
CrushFTP and other servers use a "keystore" to hold the chain of keys, and these have a way to link the keys together. CrushFTP will accept either a JavaKeyStore (JKS) or a PFX, P12, (PKCS12) formatted keystore. A keystore is like a folder of keys, but with a password on the folder of keys to secure them.
So a keystore needs a private key in it, plus the root cert, plus the intermediate cert, and finally your signed cert.
So going from apache individual files to a keystore is a documented process of a few steps. You basically are importing the files into a PKCS12 keystore. Then CrushFTP can use that kesytore file directly.
A JKS keystore for practical purposes works the same as a PFX file. (Not 100% the same, but for what you care about, it is.)
Here is a link for converting Apache files into a PKCS12 file. Openssl_key_convert
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
generate.png | 56.9 kB | 1 | 05-Dec-2023 05:32 | Ben Spink | |
png |
generate_button.png | 38.0 kB | 1 | 05-Dec-2023 05:32 | Ben Spink | |
png |
import.png | 71.1 kB | 1 | 05-Dec-2023 05:32 | Ben Spink | |
jpg |
prefs_ssls1.jpg | 114.5 kB | 1 | 05-Dec-2023 05:32 | Ada Csaba | |
png |
sign.png | 75.6 kB | 1 | 05-Dec-2023 05:32 | Ben Spink |