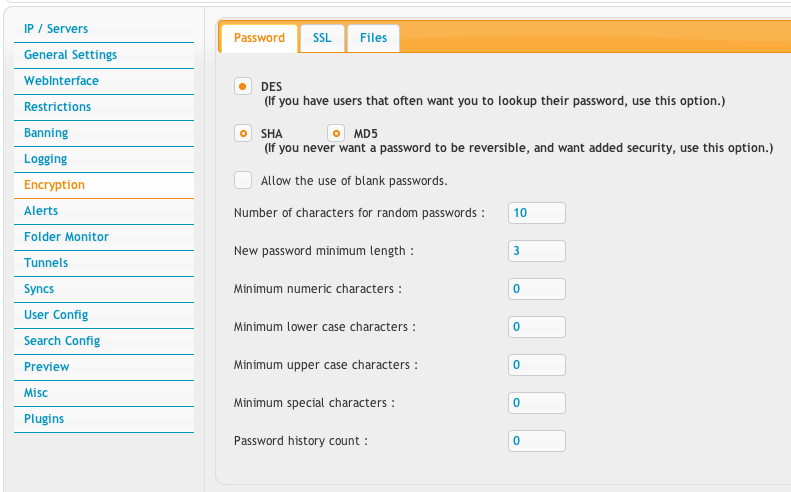
Passwords in the user manager can either be stored in DES or hashed using MD5 or SHA mode. MD5/SHA mode makes them irreversible. So neither you, nor anyone else can lookup a user's password at a later date. You can also set some restrictions on password length, and how many characters for random passwords. These are enforced anytime a user changes their password as well.
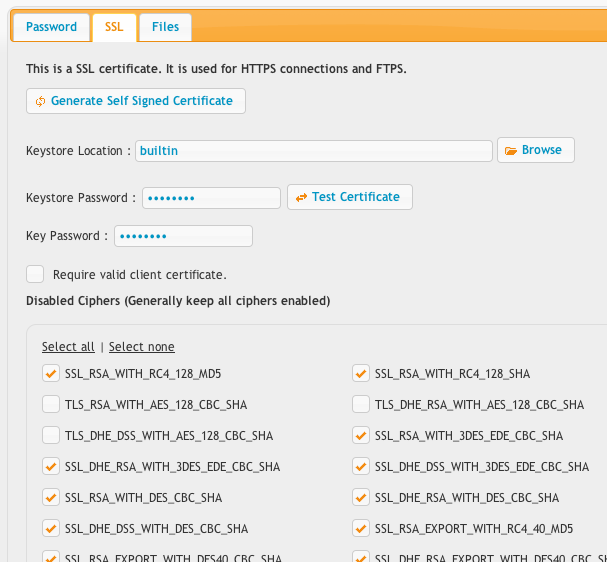
This tab lets you configure the SSL certificate used by the server. This certificate is used for SSL FTP, and HTTPS. CrushFTP comes by default with a built in self signed certificate. Users will be warned the certificate is not trusted, but after that all data is encrypted. CrushFTP expects the certificate to be in a Java keystore file (JKS) or pkcs12 PFX file and needs the password to access the keystore. If you do nothing and leave these settings at their defaults, SSL will be working. If you make changes, be sure you do so accurately. This is the global SSL cert, but you can also specify a SSL cert on individual HTTPS/FTPS ports. Requiring client certificates will block all connections fi the browser doesn't have a client cert already installed that you provided them.
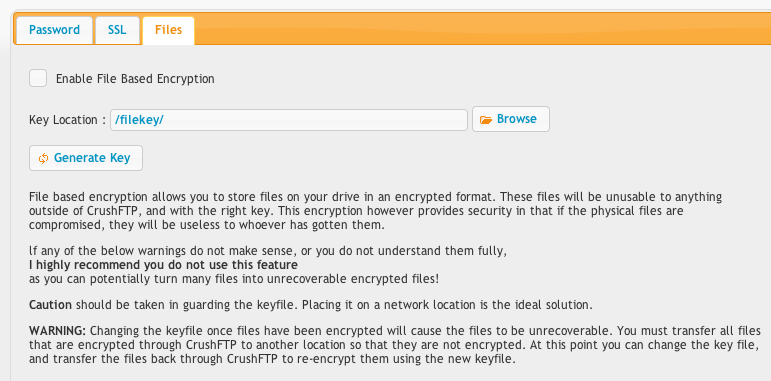
File based encryption allows you to store files on your drive in a format that cannot be read by anything outside of CrushFTP. The files are encrypted, and are only decrypted if transferred back through CrushFTP using the same key that was used to encrypt them. As the screenshot indicates, you really need to know what you are doing if you plan to use this. If you loose your key, the files all become worthless. There is also a user manager option for this on a per user basis.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
prefs_encryption_files.png | 51.5 kB | 2 | 09-Oct-2016 18:14 | Ben Spink | |
png |
prefs_encryption_password.png | 60.3 kB | 2 | 09-Oct-2016 18:14 | Ben Spink | |
png |
prefs_encryption_ssl.png | 51.7 kB | 2 | 09-Oct-2016 18:14 | Ben Spink |
