To configure AS2/3, you need to use the Java program called "keytool" to manage your certificates. Keytool is a command line program available on every OS, and it part of the Java install.
These screenshots assume the folder "/mycertificates/" contains the keystore file called "crushftp.jks" which is my private keystore containing both my public key used for encrypting and private key used for decrypting. It also assumes this folder contains "company.jks" which contains the trading partners public key used for encrypting files.
CrushFTP makes a "proxy" type of connection to do AS2/3. To send outgoing files, you use a typical FTP client and send the file to a specific directory in CrushFTP which in turn sends the file out using either AS2 or AS3.
The only difference between AS2 and AS3 is that AS3 destinations for the options is that the recipient URL starts with FTP:// or SFTP:// instead of HTTP(s)://.
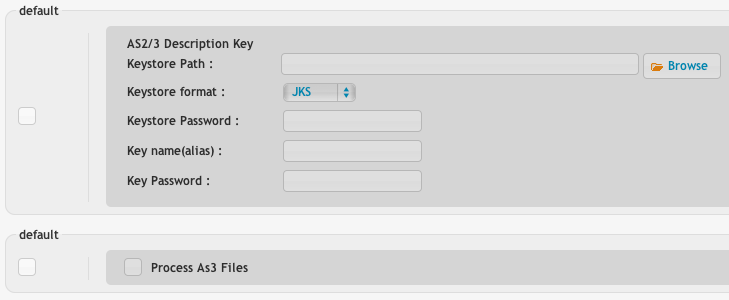
These are the settings for receiving files. Click the show all button in the user manager to see these. For incoming files, we CrushFTP requires BASIC authentication for AS2 over HTTP(s).
Next, click the mini folder icon on the left with link symbol on it. Once this window is complete, you will be able to add permissions to the item as I have done on the right here.

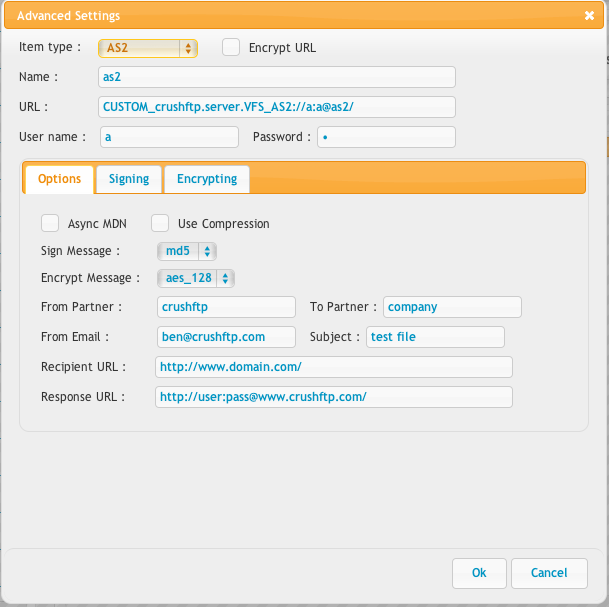
Here is where you configure your specific AS2/3 settings for this outgoing item. Cipher strengths above 128 require higher strength policy files to be installed (FAQ).
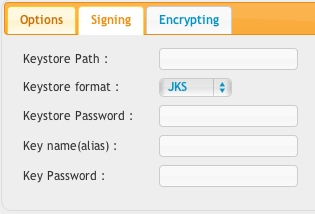
The signing keystore is your private keystore which is used to sign a message to the receiver can know it came from you.
The encryption keystore is the trading partners keystore that contains just their public certificate file. You encrypt with this file so that only they can decrypt it using their private key.
If you have your partner's public key for who you want to send to, you need to import that into a keystore file.
keytool -importcert -alias {partner_name} -file {partner_public_key_file} -keystore {partner_name}.jks
That will be the keystore you use for the encryption tab. {partner_name}.jks
For signing, and your public key you are going to give your partner...
keytool -genkeypair -alias {your_name} -keyalg RSA -keysize 1024 -keystore {your_name}.jks
Then get your public key out to give to your partner:
keytool -export -alias {your_name} -file {your_name}.cer -keystore {your_name}.jks
Send them the resulting {your_name}.cer file. That is your public key they can encrypt with. You set this keystore file {your_name}.jks on the "AS2/3 Decryption Key" panel of the user manager and on the signing tab of the VFS item.
Here is another screenshot of a complete example:
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
Encrypt.png | 78.1 kB | 2 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
Screen Shot 2013-11-23 at 1.35... | 30.3 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
Screen Shot 2013-11-23 at 1.37... | 72.2 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
as2_options.png | 55.7 kB | 2 | 25-Oct-2018 04:31 | Ben Spink | |
png |
as2_receive.png | 25.8 kB | 2 | 25-Oct-2018 04:31 | Ben Spink | |
png |
as2_signing.png | 17.1 kB | 2 | 25-Oct-2018 04:31 | Ben Spink | |
png |
complete.png | 158.7 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
delete.png | 49.4 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
exclude1.png | 42.0 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
exclude2.png | 41.1 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
find.png | 92.8 kB | 4 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
new_vfs.png | 3.6 kB | 1 | 25-Oct-2018 04:31 | Ben Spink | |
png |
options.png | 135.7 kB | 2 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
signing.png | 76.2 kB | 2 | 25-Oct-2018 04:31 | Halmágyi Árpád | |
png |
tasks.png | 47.0 kB | 1 | 25-Oct-2018 04:31 | Halmágyi Árpád |
